Hackers can create catastrophic situations if they get access to the IoT ecosystem. Therefore, it’s crucial to protect it. Azure IoT provides a secure channel for communication through authentication services.
1. End-to-end communication
End-to-end communication for IoT-based devices can be secured by utilizing the services provided by Azure. We don’t need to check for the authenticity of every user for their request, it is taken care of by Azure AD. Azure AD is Microsoft’s cloud-based identity and authentication service. Azure AD helps in signing in the user and allows access to Azure services and many SaaS-based applications. Once the user logs in to the application, they are validated by Azure AD and provided with a JWT token, which has its expiry time and is used for further communication with the IoT services.
As the user initiates the request, they must provide the JWT token in the header of the request and once the request reaches the Cloud, it is validated based on the JWT token present in the header. Upon successful validation and authentication of the JWT token, the request is sent to Azure resources like IoT-Hub, Cosmos DB, and so on.
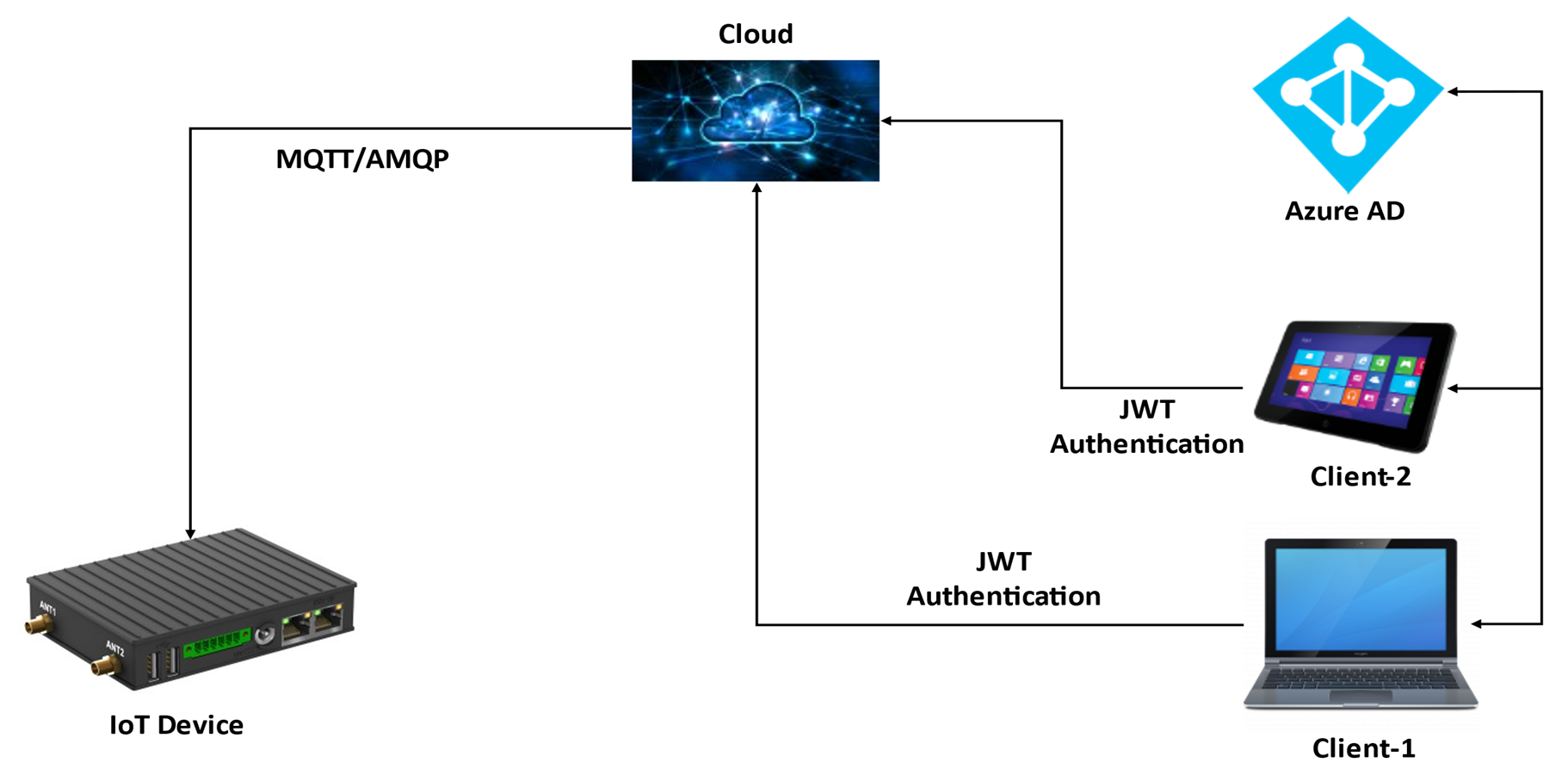
Let’s take an example of an IoT device running remotely and sending data to the user’s mobile application while performing operations based on the request generated by the user from the mobile application as shown in the diagram below.
Once the user initiates the operation from the mobile application on the IoT device from a remote location or in the same location, this request first reaches the Cloud where it is validated and authenticated against the JWT token present in its header. Once the request gets validated, it goes to the Azure resource, which in our case is the IoT-Hub.
From the IoT-Hub, the request reaches the device, and the communication channel between the IoT-Hub and the device is secured as it uses the MQTT/AMQP protocol for communication. This way the entire communication channel between the IoT device and mobile application is secured.
2. Device provisioning security
The first part of any IoT application is provisioning its IoT device with Azure. This process is called the device provisioning process.
We can make the device provisioning more secure if we use the TPM-based IoT devices. This adds one more layer of device-level security to the IoT application. A Trusted Platform Module (TPM) is the specialized chip on the IoT device that helps secure the hardware with a cryptographic key.
TPM helps in providing security against threats like firmware and ransomware attacks. Azure provides Device Provisioning Services (DPS) that can be used to provision TPM-based devices. While creating the DPS, we should select the same resource group in which our IoT Hub is being created. Once the DPS is created, we need to link the IoT-Hub. To link the IoT-Hub from the settings menu go to the linked IoT hubs section and click on the add button and from the dropdown select your IoT-Hub.
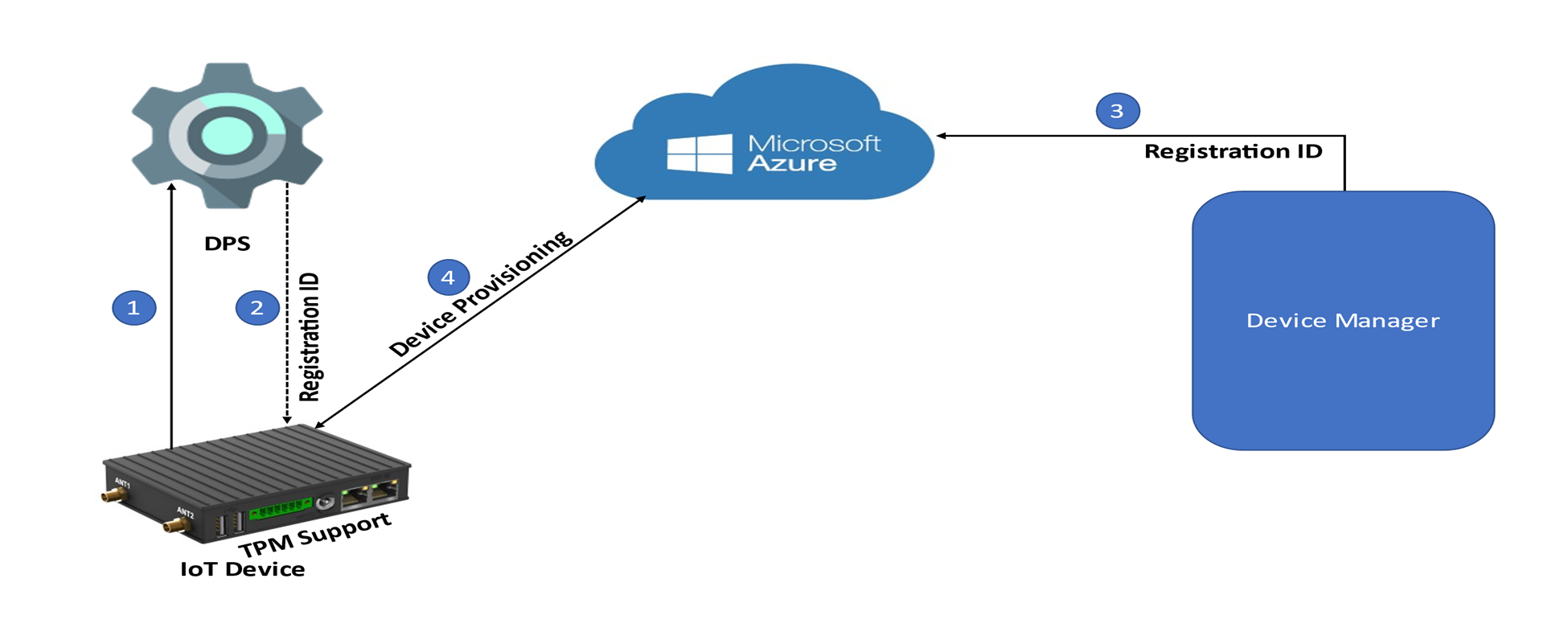
To understand the TPM-based device provisioning, refer to the below diagram. The first step of provisioning in the TPM-based device is enrolling the IoT device with the DPS. As a part of the enrolling process, your IoT device is registered with the DPS and it provides a unique id, referred to here as the registration id.
This registration id is used while creating a device from the device manager. Once you have created the device using the registration id from the device manager, it is created on the IoT-Hub. Once the IoT device boots up, it gets provisioned.
If we are using a Linux-based IoT device, then we have the liberty to add more hardening rules to that IoT device to make it more secure. We can add the below-mentioned additional securities to the Linux-based IoT device.
- Disable IPv6 (if not getting used).
- Block USB ports.
- Add IP table rules to configure the firewall to block XMAS packets, and syn-flood packets, and enable bad error message protection.
- Allow communication on the ports that are being used by the application and block all other ports. Block the ICMP incoming packets.
eInfochips provides a variety of services to build an end-to-end IoT ecosystem for your business. We provide services in the IoT Cloud back-end, device firmware, device management, state-of-art UI applications to manage the IoT devices, integrating services like a database (COSMOS DB, MySQL, and more), function apps, and mobile applications. We are proficient in developing IoT solutions and Services with enterprise-grade security, scalability, reliability, and productivity on well-known Cloud providers i.e., Microsoft Azure, Amazon Web Service, & Google Cloud.
Contact our experts to know more about how we can help you scale up.











