BLE only transmits data in one direction. Let’s take a look at a BLE beacon attempting to communicate with a nearby smartphone. A Bluetooth beacon device periodically broadcasts data packets. Nearby smartphones using specific apps or pre-installed services can detect these data packets.
BLE data transfer is one-way communication. Let’s use a nearby smartphone as an example of a BLE beacon trying to interact with it. A Bluetooth beacon device transmits data packets at regular intervals. Nearby smartphones using specific apps or pre-installed services can detect these data packets. This BLE communication can trigger actions such as message push or app marketing. To conserve energy and provide quicker data transfer, the whole Bluetooth BLE communication structure consists of 40 frequency channels, each separated by 2MHz. Among these, three channels are classified as data channels and serve as the primary channels for commercials. The Bluetooth communication starts with these three principal advertisement channels, followed by the secondary channels.
BLE Communication
Over the past ten years, the Internet of Things (IoT) has become increasingly integrated into various systems, including industrial, healthcare, military, beacon, and smart home products. The majority of these IoT devices connect to the Internet and communicate data via BLE. Almost all recent operating systems, including Windows 10, Linux, Android, and macOS, support BLE.
Compared to other low-power wireless technologies like ZigBee, Z-wave, and Wavenis, BLE has achieved the highest level of popularity. It is more energy-efficient than its competitors, such as the ZigBee and ANT protocols. BLE stands out from other wireless technologies like Bluetooth and WiFi due to its minimal power consumption and low energy requirements. However, many of its privacy and security flaws stem from its flattened protocol stack.
Given that BLE is currently used by billions of devices, it is crucial to examine its security flaws. While these personal and commercial gadgets enhance our lives and boost productivity, they also make systems more vulnerable to attacks. The prevalence of BLE in healthcare applications raises concerns about serious security and privacy issues. Once a BLE connection is established, it is considered practically unbreakable. However, BLE devices are still susceptible to eavesdropping, pin cracking, Man-In-The-Middle (MITM) attacks, and other threats, particularly due to improper pairing, unsuitable authentication, and poor protocol implementation (e.g., lack of adequate encryption). Consequently, security flaws can lead to stolen personal data, unlocked smart locks, misinterpreted messages, IoT devices running out of battery unexpectedly, and more.
Bluetooth LE security modes
The Generic Access Protocol (GAP) for a BLE connection specifies two security modes and several security levels for each mode.
There are four levels of security in Security Mode 1, which uses encryption to establish security.
- Security Level 1 – No Security (No Encryption and No Authentication)
- Security Level 2 – Unauthenticated pairing with encryption
- Security Level 3 – Authenticated pairing with AES-CCM encryption
- Security Level 4 – Authenticated LE Secure Connections pairing with encryption. Elliptic Curve Diffie-Hellman P-256 (ECDH) and AES-CCM encryption are used at Level 4.
Data signing is used to enforce security in Security Mode 2. The single application of Security Mode 2 is connection-based data signing. There are two levels available.

Security Mode 2
- Security Level 1 – Data signing and unauthenticated pairing.
- Security Level 2 – Data signing and authenticated pairing.
How BLE5 Compares to BLE4
The platform’s versions 1 through 3 used Bluetooth radio, which consumes a significant amount of energy to function. BLE, also known as Bluetooth Low Energy, was initially developed to decrease the power consumption of Bluetooth devices. It was first introduced with Bluetooth 4.0 and continued to improve through the BLE4 series, with the most recent being 4.2. BLE5 further enhances BLE4 in terms of design and performance in a variety of ways.
Speed – BLE5 can send data at a rate of 48 Mbps. This is twice as fast as BLE4’s data rate. The maximum bandwidth of Bluetooth 5.0 is 5 Mbps, which is more than twice the bandwidth of Bluetooth 4.2’s 2.1 Mbps. As a result, BLE5’s data rate effectively increases to 2 Mbps.
Range – BLE5 has a range that can be up to four times greater than Bluetooth 4.2. The greatest range of a BLE4 solution is roughly 50 metres, thus with Bluetooth 5.0, something around 200 metres is feasible.
Broadcast Capability – With a message capacity of approximately 255 bytes (while BLE4 has a message capacity of about 31 bytes), Bluetooth 5 enables data packets that are eight times larger than those supported by the previous generation. Since there are now many more data bits in each packet, the net data throughput is likewise boosted, giving BLE5 far more capacity for its actual data load.
Compatibility – Although it does not work with Bluetooth 5 devices, BLE4 is most compatible with gadgets that support version 4 of the series. BLE5 is backwards compatible with all Bluetooth versions up to version 4.2, with the caveat that not all Bluetooth 5 capabilities may be accessible on all devices.
Power Consumption – BLE5 was created to utilise less power than BLE4 despite the fact that both BLE4 and BLE5 are components of the Bluetooth Low Energy ecosystem. Because of this, Bluetooth 5 devices may be continually used for long periods of time without incurring a significant battery drain. Smaller form-factor gadgets like IoT sensors and wearables have long had this problem. Thanks to Bluetooth 5’s better power consumption approach, the majority of these devices’ batteries will last longer.
Resiliency – BLE5 was created with the understanding that crucial Bluetooth procedures frequently take place in overloaded environments, which adversely impacts their performance. When compared to Bluetooth 4.2, BLE5 performs significantly more consistently in busy conditions.
Security – In April 2017, security experts identified numerous Bluetooth software flaws that collectively became known as “BlueBorne” and affected several operating systems, including Microsoft Windows, Google’s Android, Apple iOS, and Linux. Some of these flaws could allow an attacker to access systems or devices without authentication, thereby gaining control of the entire device. BLE5 has largely addressed this problem by implementing bit-level security and authentication rules utilizing a 128-bit key.
Connection Vulnerability of BLE
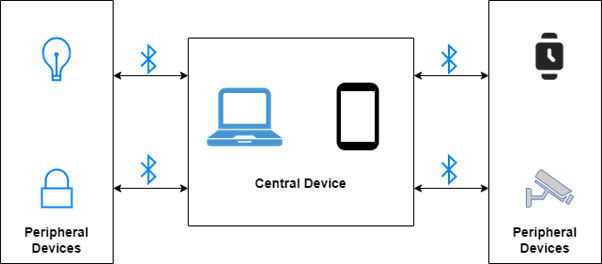
The connection setup process has two responsibilities. The Central Device is the name of the client. One or more smart terminals, frequently using operating systems, may act as the central device. For example, our smartphone often serves as a focal point. A peripheral device is the name of the server. Typically, a peripheral device is a gadget with a defined purpose, like a smart thermometer, smart lock, or smart light. If our smartphone can offer services to other devices, it may occasionally function as a peripheral. A peripheral can broadcast its presence and let other devices know it is there. In response to this advertising, the central device sends a scan request and subsequently establishes a connection.
BLE chips in devices that have previously validated a connection are incredibly difficult to exploit. However, pairing is where the greatest risk of BLE-enabled systems lies because devices must pair to connect. Devices communicate information required for authentication during the pairing process, which consists of two to three steps. This information includes keys and input/output capabilities. The third step is optional and only occurs if the devices are going to bond, which is why we say there are two to three phases. During the bonding procedure, devices save the authentication information they traded during the first pairing so they may remember each other as secure when reconnecting later.
To determine how to proceed with their connection, devices share fundamental knowledge about their capabilities during the initial phase of pairing. On the network, gadgets essentially identify themselves and describe what they are (a Fitbit, a keyboard, a headset, etc.) and what they can do. The communication is not encrypted. Key generation and exchange take place during the second pairing phase. BLE connections can be interfered with at this time. Attackers may be able to take control of devices and the data they communicate if the connection is not adequately protected. BLE’s developers have worked very hard to secure the second phase because it is such a vulnerability in connections.
Privacy
In BLE, privacy prevents other untrusted devices from tracking a particular device. The device’s ability to prevent other unauthorized devices from decoding its address determines this type of capability. If the address from the advertising phase is made public, other devices could utilize it. To maintain anonymity, two devices communicate using a private key known as the Identity Resolving Key (IRK). The peer device that keeps the IRK generates a random address that can only be resolved by that specific peer device.
A 48-bit Bluetooth device address, or BD_ADDR, is assigned to each Bluetooth device. These addresses fall into two categories: random device addresses and public device addresses. The public device address is composed of two 24-bit integers, known as a business ID and a company-assigned ID. On the other hand, the address for the random device is generated randomly and can be either a static random address or a private random address. While the private random address might change only in one power cycle, the static random address remains the same. With every connection, the secret random address could vary. The two subcategories of private random addresses are non-resolvable private addresses and resolvable private addresses. The basis for privacy in BLE is the resolvable private address (RPA).
Major Threats to Bluetooth Low Energy Security
In the years ahead, the use of BLE technology will continue to increase significantly. At the same time, it draws the attention of potential assailants. As a result, BLE security will be of the utmost importance. Bluetooth’s security architecture has evolved over time, and it wasn’t always as secure as it is now. In the past, it could be readily fabricated and might only offer minimal message integrity security.
Imagine an attacker having the ability to covertly modify the on/off switch, as shown in the heart rate monitor example above. This represents a potential MitM (Man-in-the-Middle) attack. Authentication protects against MitM by ensuring that each participant can cryptographically confirm the identity of the other. In the BLE world, when you initially connect your smartphone to an IoT device, you may encounter a “pairing” pop-up. Once two devices are paired, they save permanent settings and become “bonded,” eliminating the need for further pairing each time they attempt to connect.
During each of the three BLE pairing processes, a Temporary Key (TK) is utilized to produce a Short-Term Key (STK), which is subsequently used to encrypt the connection when a Characteristic requests encryption. The standard has defined four coupling mechanisms, known as Association Models, to accommodate different devices with distinct input/output capabilities (Core 5.2, Vol. 1, Part A, 5.2.4). Each of these mechanisms of operation has been thoroughly explained previously. Additionally, there is the idea of “connection models” that further compound the problem. While BLE versions 4.2 and up employ the Secure Connection paradigm, BLE versions 4.0 and 4.1 use a connection type currently known as LE Legacy Pairing. The overall security of these models varies due to differences in their encryption methods, key exchange systems, and authentication mechanisms. The BLE version utilized is influenced by both the Peripheral (IoT device) and the Central (smartphone).
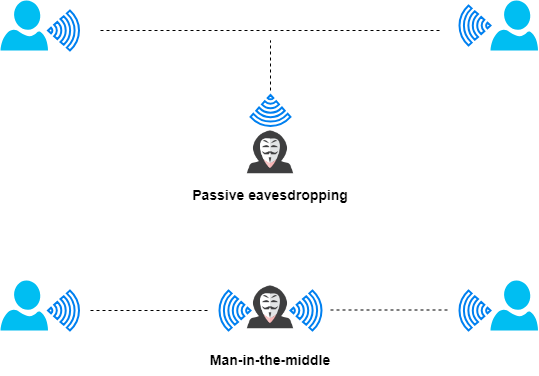
Passive eavesdropping and man-in-the-middle assaults are the two types of cyberattacks most frequently associated with the hacking of Bluetooth Low Energy modules. A BLE network can be attacked through passive eavesdropping, which allows an outside device to intercept data being exchanged between devices. For example, an attacker may listen to the data that industrial peripheral sensors provide to a central unit to find new security gaps in the system. BLE modules that make use of BLE Secure connections are, by default, protected from passive listening.
In man-in-the-middle assaults, an alien device that simultaneously assumes central and peripheral roles is used to trick other networked devices into connecting to it. This could become a problem in major manufacturing complexes as the extraterrestrial device may insert bogus data into the stream and disrupt whole production chains. BLE Secure connections provide security against passive eavesdropping, but man-in-the-middle attacks can only be stopped with the right pairing technique.
Conclusion
Only when correctly implemented is Bluetooth Low Energy a secure wireless communication standard. The second step of pairing is the only real point of vulnerability, although you can always make this phase safe by using a suitable pairing technique. There are two methods that hackers could use to gain an advantage in a BLE network: first, they introduce hostile alien devices to take control of the entire network, which is known as a man-in-the-middle attack, or they passively listen to the data broadcast on the network, a practice known as passive eavesdropping.
When developing IoT applications, as a service-based organization, we can apply security measures through the IoT protocols to create safe and reliable applications. This is accomplished by considering the security needs of the protocols on which the IoT ecosystem entirely depends.
Businesses considering developing and deploying IoT ecosystems should always understand the fundamentals of IoT security. A good structure must have a strong foundation, as the adage goes. To create sophisticated applications, we must start with a solid foundation, as common flaws, rather than sophisticated algorithms, might be exploited by attackers, resulting in significant commercial losses.
eInfochips offers end-to-end IoT Solution and Services in a variety of industries. With their strong experience and in-depth understanding of connection protocols and industry standards, eInfochips assists clients in properly securing IoT protocols. Among other cybersecurity services, they also offer VAPT and Security Implementation, Assessment Consulting, and Managed Security Services. Speak with their specialists to learn more about their services. Get in touch with us













