One of the biggest risks to corporate data security today is the rise of fileless malware. This type of malware is becoming increasingly prevalent, but it poses a challenge for attackers as it is more complex than conventional malware. To use this type of malware effectively, attackers must have advanced skills and knowledge in building and deploying it. Fileless malware attacks are carried out often by the most sophisticated cybercriminals or state-sponsored actors.
Developing fileless threats requires specialized skills due to the limitations of device memory and disk space. The infection is limited to a small area of memory, making it difficult for attackers to find enough space to install it. Moreover, fileless malware is erased from memory every time the system is rebooted, so it must work quickly. For attackers to be successful with fileless malware, all the right conditions must be in place.
According to a report by Globenewswire, the number of fileless malware attacks saw a staggering increase of almost 900% in the year 2020.
Protecting your organization against the fileless malware attack is critical in today’s digital landscape.
WHAT IS A FILELESS MALWARE?
Malicious software, known as fileless malware, is a RAM-based artifact that resides in a computer’s memory. In other words, fileless malware leverages the weaknesses in installed software to carry out an attack. This type of harmful behavior makes use of native and legitimate tools that are already present on a system to conduct a cyberattack. Unlike traditional malware, fileless malware does not require the attacker to install any code on the target machine, making it more challenging to detect.
The terms “in-memory malware” and “fileless malware” are often used interchangeably because both operate without ever writing any data to disk. This means that the malware operates solely in the memory of the computer, making it difficult to detect and remove.
Fileless malware is a type of threat that doesn’t reside on the hard drive. However, this comparison is not entirely accurate. The key difference lies in the mechanism of infection and persistence, even though the behavioral execution environment is similar in both cases, i.e., both malware versions are executed in system memory.
The majority of malware’s infection vectors, such as infected file attachments, external media devices like USB drives, peripherals, mobile phones, browser drive-by attacks, side-channels, etc., involve writing to the hard drive-in order for it to be executed.
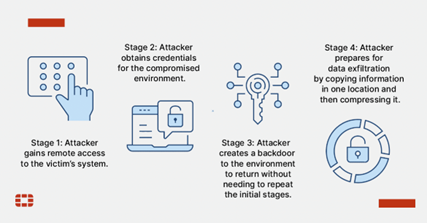
How Does Fileless Malware Attackers Operate?
Step 1: Gain Access
The attacker first establishes a foothold in the victim’s system by obtaining remote access.
Step 2: Steal Credentials
With the access gained in the previous step, the attacker tries to obtain credentials for the compromised environment, allowing them to move on to other systems within that environment quickly.
Step 3: Maintain Persistence
The attacker creates a backdoor that allows them to revisit the environment at any time without repeating the attack’s initial stages.
Step 4: Exfiltrate Data
The attacker gathers the desired data, consolidates it in one location, and uses readily available tools such as Compact to compress it before exfiltration. The attacker then transfers the data over FTP to remove it from the victim’s environment.
Common Techniques of Fileless Malware Attacks
Fileless malware infiltrates systems by disguising itself as legitimate software. It then leverages the tools already present on the system to carry out its attack. These types of attacks pose a significant risk to organizations, as fileless malware operates in the memory of a machine and never writes any code to the hard drive.
This makes it similar to other forms of malicious software in terms of how it enters a system, but also more challenging to detect and remediate. Conventional malware detection methods may miss it, as it utilizes Windows PowerShell and Windows Management Instrumentation (WMI), operates in memory, and behaves like normal programs.
Once established, fileless malware can spread laterally across a network, potentially giving attackers access to sensitive data or the ability to disrupt an organization’s operations. The most attractive aspect of fileless malware from the attacker’s perspective is its ability to infect a machine without bypassing antivirus software.
This is because fileless malware modifies command lines, which are lines of code that instruct programs what actions to take. As there are no unusual files associated with the threat, a standard antivirus application may not be able to detect it. By infiltrating memory, fileless malware can execute dangerous code and move around a network.
Exploit Kits
Exploit kits are collections of code fragments, command sequences, or data collections that take advantage of known vulnerabilities in software or operating systems. These tools are utilized by attackers to launch successful attacks.
Registry Resident Malware
Registry resident malware is a type of malware that infects the Windows registry and hides itself to remain persistent and undetected.
Memory-only Malware
Memory-only malware is a type of malware that exists solely in the memory of a computer, without leaving any trace on the hard drive.
Ransomware
Ransomware attacks are increasingly using fileless methods to insert malicious code into documents through native scripting languages such as macros, or by directly injecting harmful code into memory through exploits.
Detection Of Fileless Malware
Removing fileless malware is a challenging task, as it operates without leaving a trace on the hard drive. To detect its presence, security teams must perform an analysis of the code currently running in memory, looking for Indicators of Attack (IOA) such as code execution, lateral movements, and behavior designed to conceal its intentions. Memory analysis is the only way to accurately identify and validate the presence of fileless threats, providing security teams with crucial information about the malware’s use and the damage it has caused.
To Reduce The Risks Of Fileless Malware
There isn’t a straightforward, up-to-date virus definition file or comprehensive antivirus program that can prevent attacks from fileless malware attackers. As trusted legacy antivirus solutions become less effective, it will be necessary to install next-generation endpoint security solutions that are currently being developed.
These Endpoint detection and response (EDR) systems rely on ongoing, real-time monitoring of phishing emails, incoming and outgoing network traffic, and suspicious activities in programs like WMI and PowerShell. The study and detection of user and system activity are crucial to security, as these fileless attacks often exploit human susceptibility. On a personal level, important best practices include:
- Being cautious when downloading and installing applications.
- Staying up to date with security patches and software updates.
- Updating browsers regularly.
- Being aware of phishing emails.
Organizations must adopt a more sophisticated security architecture, as traditional antivirus and endpoint security products cannot detect fileless threats. Implementing zero-trust policies and strong multi-layered protection systems is the best approach.
There are three primary components to consider when addressing cybersecurity
Analyze your current security framework
The first step is to conduct a thorough review of administrative rights and privileges and adjust settings for least privileged access. Unneeded or unnecessary components should be disabled or removed, and core systems should be updated with the latest security patches.
Utilize the right security tools
Multi-factor authentication (MFA) and robust authentication and identity management are essential. Point security technologies can mitigate certain hazards, such as malware delivered via email. Consider incorporating machine learning (ML) and artificial intelligence (AI) to detect unusual activity, such as network alterations, and implement behavioral monitoring. Tools for scanning memory are also available.
Educate and train staff
According to ISACA’s 2022 State of Cybersecurity Report, nearly 70% of cybersecurity professionals feel that their company’s cybersecurity team is understaffed, a significant increase from the previous year’s 61%.
Cybersecurity awareness training is also crucial. Employees need to understand how to identify phishing emails and the dangers of clicking on suspicious links. While there is no single solution to prevent fileless malware and LotL attacks, a comprehensive security strategy can reduce the risks.
eInfochips provides comprehensive cybersecurity services for threat modeling, Vulnerability Assessment and Penetration Testing (VAPT) for devices, OS/firmware, web/mobile applications, data, and cloud workloads. These services include the detection and classification of malware using machine learning techniques such as signature-based algorithms, feature extraction, static analysis, and dynamic analysis, among others.
The company employs a variety of tools, including Virustotal, Process Monitor, Regshot, Wireshark, and Procmon, to categorize several types of malwares, such as trojans, backdoors, viruses and worms, rootkits, etc. This approach helps clients deliver secure products to the market and protects them against malicious software.
eInfochips has helped companies worldwide to develop, implement, and manage security solutions that comply with security industry standards, regulations, and guidelines, such as NIST (National Institute of Standards and Technology), ENISA (European Network and Information Security Agency), OWASP (Open Web Application Security Project), MITRE (Massachusetts Institute of Technology Research and Engineering), and the IoT Security Foundation.
References:
1. https://www.fortinet.com/blog/industry-trends/fileless-malware-what-it-is-and-how-it-works
2. https://www.csoonline.com/article/3227046/what-is-a-fileless-attack-how-hackers-invade-systems-without-installing-software .html
3. https://www.google.com/search?q=fileless+malware&rlz=1C1GCEA_ enIN1015IN1015&oq= Fileless&aqs=chrome.0.35i39j69i57j0i512l5j69i60.4085j0j7& sourceid=chrome&ie=UTF-8
4. https://us.norton.com/blog/malware/what-is-fileless-malware















