Along with many technological, environmental, and economic benefits, the rapidly moving connected world also represents an array of growing attacks like side-channel attacks, fault attacks, physical tampering, etc. Considering these risks, ensuring security and robustness of IoT becomes inevitable, in which IoT gateways play an important role.
IoT Gateways are undoubtedly the heroes of whole IoT paradigm, as they are the key piece of data collection in the connected system. In IoT ecosystem, security is the key aspect, in which, IoT gateway security is of prime importance since a secured gateway enables robustness of the entire IoT environment. If there are no sufficient security measures, there are chances of potential risks like malicious threats, spoofing, man-in-the-middle (MITM) attacks, data snooping, etc. If you lose a gateway in the middle of the communication chain, it will jeopardize the entire IoT ecosystem as gateway act as a gate or bridge between the edge devices and cloud.
So how do you know whether your IoT gateway is secure or not?
Listed below are some common questions related to the security of IoT gateways. If your concern matches with any of the below questions, then there is the need to consider gateway security for your IoT ecosystem:
- How can edge device sense and prohibit unsecured gateways, or vice versa?
- How can peripherals ensure their data are successfully relayed in the face of gateways?
- What happens if someone snoops the data from the gateway?
- What if the gateway is located in a remote location and is sending incorrect information to the cloud? In this case, how can gateways help in reverting information?
- Is it possible for gateways to build and demonstrate reputation-based trust?
Trustworthiness of gateway is the key aspect in the IoT ecosystem. To overcome the security concern, let’s explore some of the key hardware security aspects that can be implemented to secure IoT gateways.
TPM (Trusted Platform Module)
What is TPM?
It is a microprocessor that integrates with system hardware on a gateway to perform crypto operations, such as key generation, key storage and protects small amounts of sensitive information, such as passwords, measurement data for boot software and cryptographic keys to provide hardware-based security.
How does it work?
TPM is often built into a system to provide hardware-based security. It is a combination of hardware and software to protect credentials when they are in unencrypted form. TPM is based on a trusted execution environment (hardware root of trust) that provides secure storage of credentials and protected execution of cryptographic operations. It is isolated from the main CPU and implemented either as a discrete chip, a security coprocessor or in firmware.
- Microprocessor scans the firmware and validates the key. If the key is valid, then the processor begins executing the firmware, but if not then, processor halts.
- The TPM is used to store platform measurements that help ensure that the platform remains trustworthy. It contains a set of registers that comprise of RTM measurements for launch modules of the boot software.
- The computing platform must have a root of trust for measurement (RTM) that is implicitly trusted to provide an accurate validation of the boot code modules. The TPM provides the root of trust for reporting and a root of trust storage for the RTMs. The TPM stores a set of “known good” measurements of boot components that are securely generated and stored.
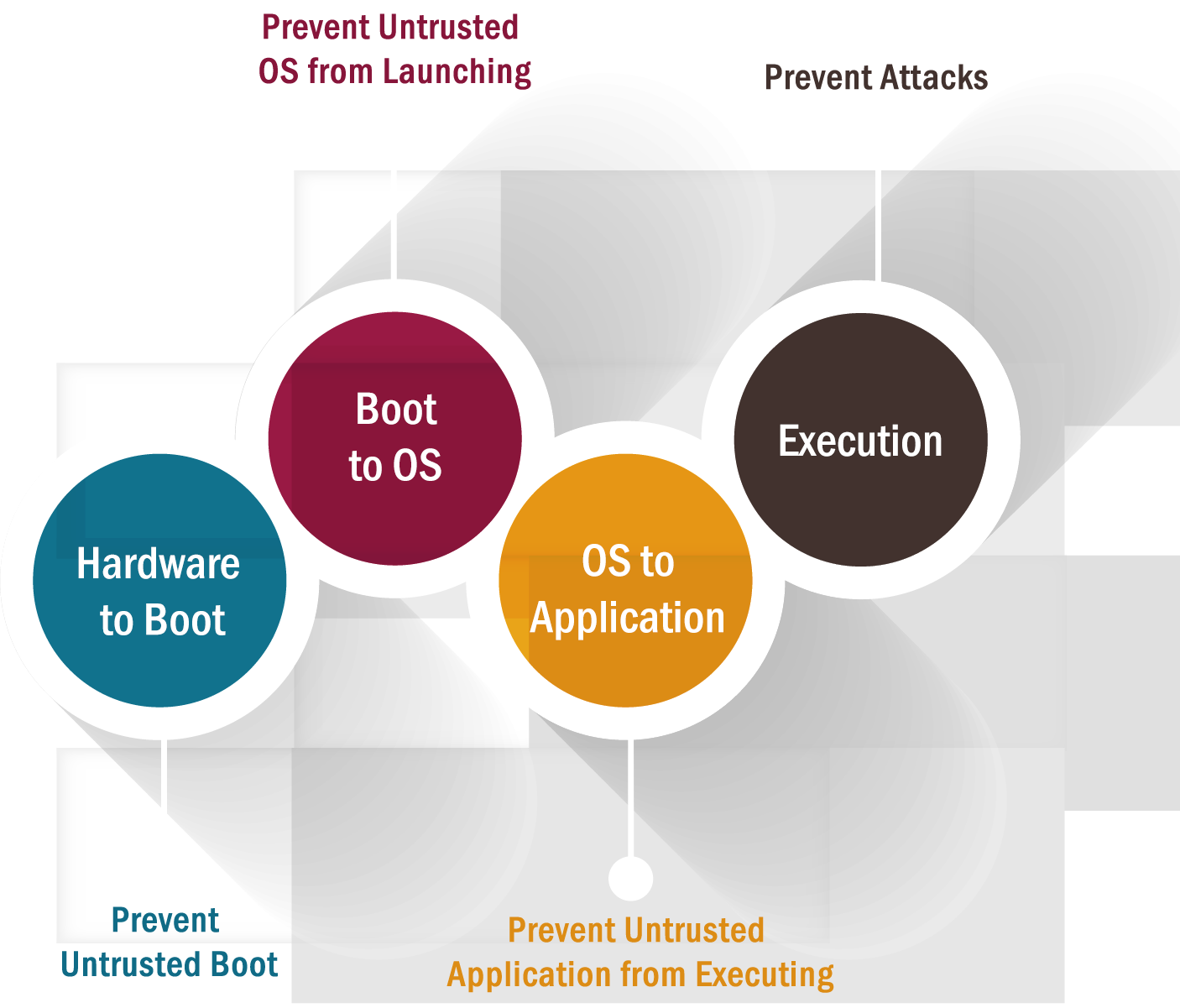
Hardware Root of Trust/Chain of Trust: It is the fundamental part of secured computing. The secure boot process is utilized to implement a chain of trust.
- Bootstrapping is a secure system or device that involves a chain of steps, where each step relies on the accuracy and security of the previous one. At the end of the chain, you assume or verify the correctness of the last step – this step becomes the Root of Trust (RoT). The Root of Trust is provided by hardware services, including cryptographic support, secure key storage, secure signature storage, and secure access to trusted functions. This allows the creation of a trusted module forming the basis, or root, for validating other components within the system. The chain of trust begins with the bootloader. From this boot loader, the OS is validated, and from the OS, the applications are validated, creating a chain of trusted elements.
TEE (Trusted Execution Environment)
What is TEE?
DOWNLOAD CASE STUDY
Enabling Remote Monitoring & Predictive Maintenance of Warehouse Equipment
The TEE is an insulated and secure area of the main processor providing security functionality for application integrity and confidentiality. The TEE differentiates between security functionality and operational functionality.
How does it work?
- It mainly consists of three parts: Trusted OS, internal micro-kernel, and APIs. Used for security check parallel to standard OS.
- Common security functions include isolated execution of security operations, the integrity of code loaded and data stored and confidentiality of data stored in the TEE. It protects data-at-rest and data-in-use within the TEE.
- It also provides higher performance and access to a large amount of memory.

Security properties that TEE can achieve
- Isolated execution
- Secure storage
- Device identification
- Device authentication
- Platform integrity
All the above security properties can be achieved using the measured boot, secured boot, and attestation.
- Secured Boot: It is a security standard verified by the trusted OEMs that ensures authenticity and integrity of a device’s boot. When the first boot happens, only the validated code from the device OEM is allowed to run to verify and validate the authenticity of software present in the gateway. This prevents attackers from replacing the firmware with versions created to perform malicious operations. It provides the APIs required for code signing, code validation, and secure firmware updates.
- Measured Boot: Measured boot is generally used for integrity protection. As anti-malware software has become better at detecting runtime malware, attackers are also becoming better at creating rootkits that can hide from detection. Detecting malware that starts early in the boot cycle is a challenge. At this time, measured boot measures each block, from firmware up through the boot start drivers, stores those measurements on the hardware, and then makes a log that can be tested remotely to verify the boot state of the client.
- Attestation: In cloud computing scenario, attestation is an essential and interesting parameter, often rooted in having trusted hardware component to build trusted system. It is basically used in the process of validating integrity in terms of software and information for securing embedded systems. Attestation uses cryptography identity techniques that confirm the identity and authentication credentials of remote devices, without revealing the devices and their own identities.
IoT gateways are crucial to addressing the inherent complexity. By using the pre-ensured hardware building blocks like TEE and TPM, you can secure the whole communication chain from the connectivity of legacy devices, data storage on a gateway, secure data transmission as well as the fast deployment of data on the cloud to perform intelligent analytics. There should be some programmable architecture that ensures confidentiality and integrity against specific attacks. So, layered IoT gateway security is essential.
At eInfochips, we are helping fortune 500 companies and enterprises to build secure IoT solutions and Services by enabling a layered security paradigm. For more information on our security capabilities, visit: From edge to cloud: A comprehensive look at IoT device security













