Introduction
Cyber threats are a constant assault on organizations, ranging from ransomware attacks and data breaches to phishing scams and insider threats. Therefore, it is crucial to develop a robust and efficient Security Operations Centre (SOC). Incident response playbooks become essential instruments in streamlining the handling and mitigation of cybersecurity incidents.
An incident response playbook is a written set of instructions that we can refer to when managing a security incident. To obtain a precise and predetermined list of steps that must be completed to prevent security issues, it is imperative that a process be followed. It also helps in understanding how an organization manages security incidents and allocates and maximizes resources. An incident response playbook’s primary objective is to guarantee that security incidents are handled efficiently. Its scope comprises responsibilities, protocols, and actions for various incident types, including incident detection, eradication, recovery, and post-event analysis.
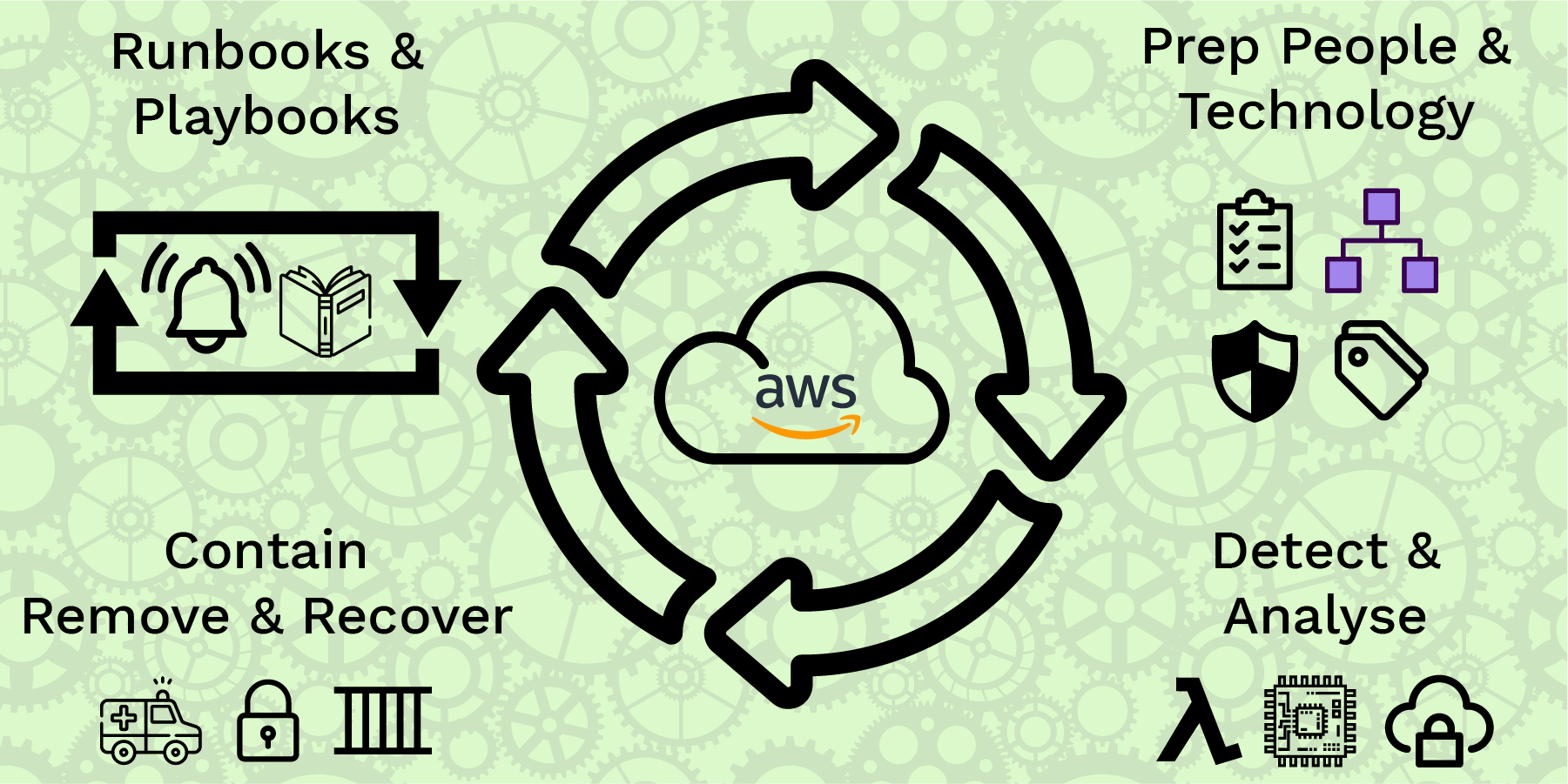
Key Components of Incident Response Playbooks
- Identification and Classification: A process for quickly determining the type and seriousness of occurrences is at the core of every playbook. In this initial stage, the potential impact of the incident is assessed, which then guides the SOC team in prioritizing the appropriate response actions.
- Escalation Protocols: It’s critical to escalate difficult occurrences as soon as possible. Playbooks describe the escalation and decision-making hierarchy, ensuring that the relevant people are notified immediately when a major incident arises.
- Eradication and Containment: The playbook outlines what must be done to stop an incident from spreading after it has been recognized. Isolating compromised systems, blocking unauthorized access, or blocking abused communication channels are a few examples of containment tactics.
- Evidence Preservation: Playbooks emphasize the critical importance of securing any digital evidence related to the incident. This thorough documentation supports prospective legal processes and forensic analysis, among other uses.
- Communication: Incident management is built on effective communication. Playbooks specify the times and means of communication with different internal and external stakeholders. Open communication promotes trust and aids in event impact management.
- Analysis and Root Cause Identification: Post-incident containment, a comprehensive analysis is conducted to determine the incident’s primary cause. This is a critical step in both fixing the current problem and averting future recurrences.
- Remediation and Recovery: The playbook outlines procedures for regaining normalcy throughout the recovery phase. It includes tasks such as restoring the system, restoring data from backups, and fixing vulnerabilities that might have been abused.
- Post-event evaluation: A thorough post-event evaluation is necessary following an incident. Playbooks require self-reflection to determine what happened, what went well, and how the reaction could be improved.

Benefits of Incident Response Playbooks
- Efficiency and Consistency: Playbooks provide uniformity to incident response protocols, guaranteeing that each member of the team adheres to established protocols. Response activities are coordinated and effective because of this consistency.
- Continuous Learning: A culture of continuous improvement is fostered via post-incident reviews. Organizations can gradually refine their incident response methods with the help of the insights gathered from each occurrence.
- Improved Cooperation: Playbooks promote cooperation between various teams inside a company. During the chaos of an emergency, collaborative efforts are encouraged by clearly defined roles and duties.
- Reduced Response Time: SOC teams may respond to incidents quickly because of predefined actions. Prompt action greatly reduces the effect of persistent threats and breaches.
- Tailored Adaptability: Playbooks can be modified to meet the unique risks and environment of an organization, ensuring that responses are made specifically to counteract different threats.
Conclusion
Incident response playbook is an essential tool to ensure that businesses are ready to handle security problems efficiently. It offers a methodical framework for reactionary actions, facilitating stakeholder cooperation and communication. It facilitates quick and uniform reactions, reducing response times and lessening the effect of incidents by providing predetermined protocols and templates. The playbook encourages a culture of learning and resilience by emphasizing post-event analysis and continuous development, which helps organizations modify and enhance their incident response skills over time. In today’s dynamic threat landscape, the incident response playbook is an invaluable tool for boosting cyber resilience and protecting against new threats













