Every connected device works on a defined protocol such as the TCP, UDP, and so on. The network topologies specify the connected devices/components with different defined terminologies under each topology. When we connect anything to a network and use specific protocols, it is not always possible to ensure data and connection security. This gives attackers a chance to breach the system and manipulate the data’s Confidentiality, Integrity, and Availability.
When we talk about the IoT (Internet of Things), we enter the larger spectrum of connectivity, where along with the computer or mobile devices, various other daily usage devices such as air conditioners, water purifiers, cars, TVs, and lights are also connected.
Table of Contents
- IoT Architecture Overview
- IoT protocols
- OS4I
- BLE
- ZigBee
- Z-Wave
- Wireless Hart
In such a broad connectivity range, we do not use the generic protocols like the TCP and the UDP. Industry specialists have developed protocols specific to the implementation of connected things. These protocols come in handy to address the gaps and loopholes. However, these protocols are equipped with security mechanisms that help the basic secured implementation during the development of an application and let them connect to “thing”.
IoT Architecture Overview
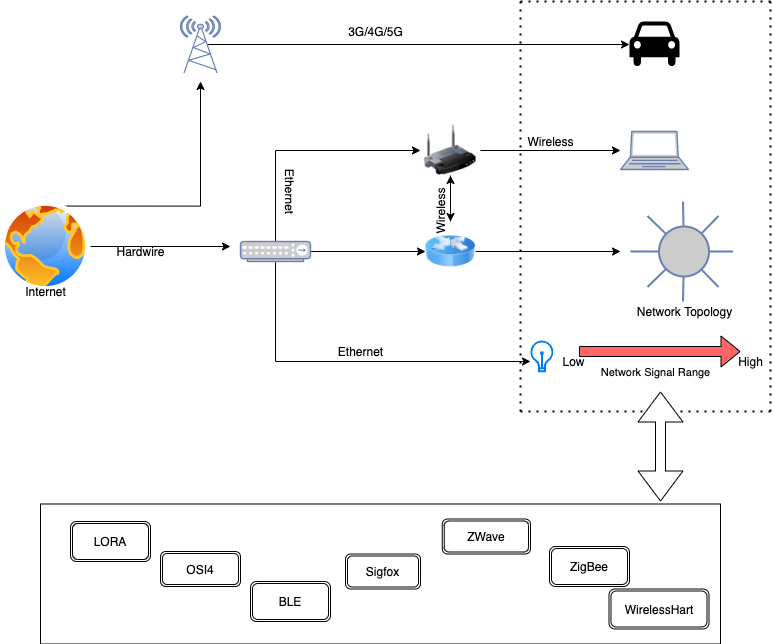
The IoT architecture is quite like the generic network architecture, where everything is connected to a wireless gateway through the Internet. The major difference is that when we examine the architecture in depth, we see that the gateway connects to the Internet on one end, but it also connects to smart devices, and a network topology. All this is possible due to the presence of specifically developed protocols.
Each protocol has its use and implementation, as well as it’s set of security standards. Let’s take a closer look at each protocol’s role and how the built-in security features can be used to achieve basic security on the Internet of Things.
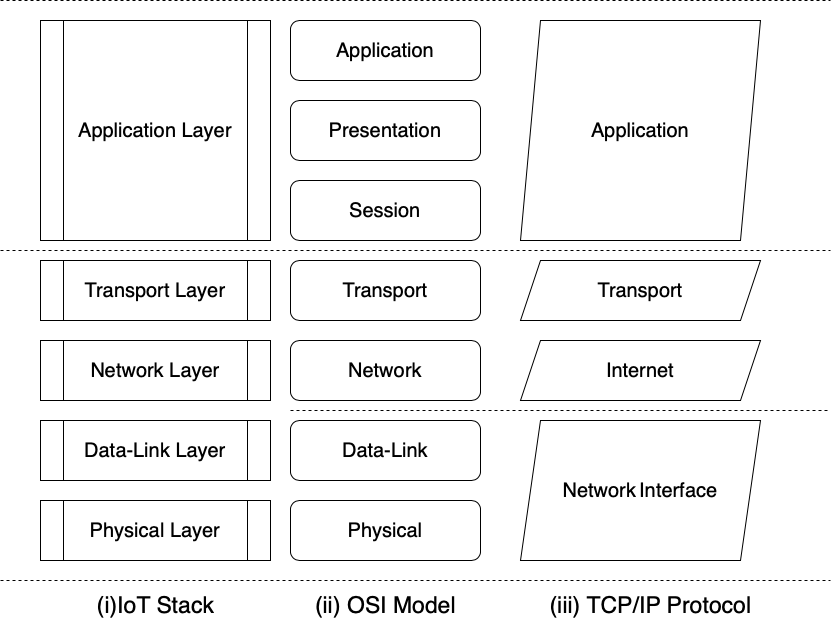
Here is a quick comparison on how the IoT Stack is related to the OSI and TCP models, to understand the functioning of these protocols in detail:
IoT protocols
IoT protocols ̶ the rules on which the IoT connectivity depends, the security on different layers will be different compared to the Generic Models we use. Let’s first classify the protocols and then get into the details of each.
These protocols are broadly classified as follows:
- OS4I
- BLE
- ZigBee
- Z-Wave
- Wireless Hart
Every protocol listed is restricted to an area of functioning, a range of connectivity, and specific relation with the basic network connectivity models.
OS4I
OS4I protocol combines different protocols to attain interoperability, data transfer, and network level connectivity. It combines protocols such as MQTT, TCP, 6LoWPAN, and IEEE 802.15.4, to work on the application, transport, network, data link, and the physical layer respectively.
As the protocol is a combination of protocols on each layer that is individually secured, it provides robust security throughout.
Security in OS4I
The security of this protocol is unique in that each layer uses an independent security mechanism. Let’s take a look at each layer of this protocol and the security that comes built-in with the specific layers.
- Security in network layer: As the network communication takes place using IPV4 and IPV6, IP security is the only security mechanism that can be applied for a secure communication.
- Security in transport layer: The transport layer uses the SSL/TLS mechanism for security. SSL/TLS is implemented to secure the transport layer function such as the TCP/UDP (User Datagram Protocol) implementation.
BLE
BLE (Bluetooth Low Energy) works on low power and is suitable for short range communication similar to the classic Bluetooth. This functionality of low energy consumption and short range make it suitable for the IoT implementations.
BLE protocol is used to communicate, monitor, and control the applications in a short radius wirelessly, with a range of up to 100 meters and it works on 2.4 GHz frequency.
Security in BLE
BLE comprises of multiple security modes with security levels. The levels and modes of security depend upon the pairing method used between the devices to connect.
BLE security is classified into two modes with multiple levels of security for each mode as follows:
- Security mode 1: The security in this mode is provided based on the encryption implemented on the four security levels.
- L1: No security: No encryption or authentication mechanism is enforced.
- L2: Unauthenticated pairing with encryption: Encryption implemented in the connection, but no authentication mechanism is enforced.
- L3: Authenticated pairing with encryption: Both encryption and well as authentication mechanism are enforced to achieve high level of security.
- L4: Authenticated secure connections pairing with encryption: An extra security mechanism of secure pairing is enforced to make the connection highly secured.
- Security mode 2: The security in this mode is achieved by data signing and thus, it has two security levels.
- L1: Unauthenticated pairing with implementation of cryptography: The authentication mechanism is not implemented but data signing is done.
- L2: Authenticated pairing with implementation of cryptography: Authentication mechanism is enforced as well as data signing is implemented.
Zigbee
Zigbee is a wireless protocol developed to address the needs of low cost and power wireless IoT networks. This protocol operates in the IEEE 802.15.4 standard and helps achieve longer battery life due to low duty cycle. It supports point-to-point communication, as well as mesh topologies, has low latency, ranges up to 300 meters and works on 2.4GHz frequency with AES128 bit network layer encryption.
Security in Zigbee
As ZigBee operates on open trust model, hence, each layer goes hand in hand for trusting the security.
Zigbee security is achieved by two types of encryption keys:
- Network key: Used to broadcast secured communication by sharing 128 bit key among all devices.
- Link key: Used to secure unicast communication on application layer by sharing 128 bit key.
The above two types of encryptions help the protocol to share the keys among the devices keeping the communication encrypted and secured.
Z-Wave
Z-Wave is a home-automation protocol developed by Zensys. The Z-Wave protocol works on the network and application layers. It uses the frequency key shifting modulation and operates at 868.42 MHz, has a radius of 100 meters, and follows mesh topology for connectivity.
Security in Z-Wave
Communication in Z-wave is sent via plain text. As it comes without default encryption that allows the interception, collection, and decoding of the unencrypted message, making the data vulnerable to manipulation.
The fifth generation Z-Wave devices come with security implementations, where HomeID provides the functionality of identifying the network uniquely and takes explicit action to add a new device to the network.
The latest Sigma design supports the 128-AES encryption and provides secure pairing feature for extra implementation security.
Wireless Hart
The Wireless Hart protocol is exclusively designed for the automation and manufacturing industries, as it was initially developed to be compatible with the IoT networks, to address the power consumption and scalability criteria.
Security in Wireless Hart
In Wireless Hart, the security services are handled at the MAC (Medium Access control) and Network layers, and each layer ensures security features.
The network layer uses cryptographic keys to maintain data integrity and confidentiality and ensure secured communication between nodes.
The Keys used for Security Implementation:
- Public key: Generates message integrity code on the MAC layer by connecting the devices.
- Network key: Used for authentication among shared devices over the network.
- Join key: Used by individual device to join the network for the first time.
- Session key: Used to ensure secured connection within the network and devices.
Conclusion
As a service-based company, when it comes to development of the IoT application, we can implement the security measures with respect to the IoT protocols to deliver secure and robust application. This is done by taking into consideration the security requirements of these protocols, which the IoT ecosystem entirely depends on.
Organizations that are considering to develop and looking implement the IoT ecosystems, should always be up to date regarding the security basics for the IoT. As they say, to build a great structure you need a strong base. So, to build complex and hi-tech applications, we should have a strong base, as the attackers can exploit the most common weaknesses and not the complex algorithm, leading to major product losses.
eInfochips provides end-to-end security solutions across various domains. With strong expertise and in-depth knowledge in connectivity protocols and industry standards, eInfochips help client secure the IoT protocol effectively. We also provide Cybersecurity services like VAPT and Security Implementation, Assessment Consulting, Managed security services, among others. To know more about our services, talk to our experts.