The security of IoT devices is a growing issue as they become more prevalent. Many of these devices are not secure by default, and they often lack basic security features such as authentication and encryption. Due to this, the security of the devices and the data they gather may be compromised by attackers. According to a survey by Keyfactor, cyberattacks have cost 89% of respondents’ organizations that run IoT and connected products an average of $250K.
Several actions may be performed to increase the security of IoT devices. These include ensuring that devices are properly configured and updated, using security features such as authentication and encryption, and monitoring devices for suspicious activity.
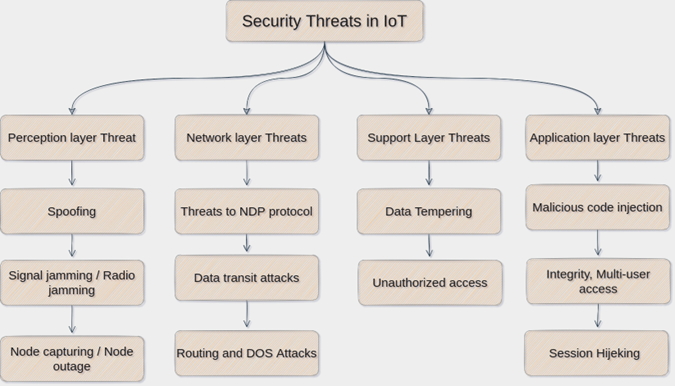
IoT Security Threats
The vast majority of IoT threats are mundane and low-risk, but there are a few high-impact threats that could cause serious damage.
The possibility of hackers accessing sensitive information stored on IoT devices is one serious threat. This could include personal information (such as names, addresses, and passwords), financial information (such as bank account numbers and credit card numbers), or even sensitive military information (such as troop movements and strategic plans).
Another high-impact threat is the potential for rogue devices to be installed on corporate networks or government institutions. These devices might be used to break into some other systems and steal confidential information.
Finally, IoT devices can be exploited by hackers to launch cyberattacks on other systems. This could include accessing private information, stealing money or data, or attacking critical infrastructure systems.
IoT security threats come in a variety of forms, from simple password breaches to more sophisticated attacks that exploit vulnerabilities in IoT devices.
IoT security risks that are frequently observed include:
- In-vehicle security breaches: A recent study found that more than 50% of drivers in the US are at risk of being hacked, and many of these attacks happen without the driver even knowing it.
- Tampering with IoT devices: One of the most common ways to exploit IoT devices is to tamper with their firmware that can result in data being lost or corrupted.
- Data theft: Another common IoT security threat is data theft, which is often done to gain access to financial or personal information.
- Insecure internet connections: A lack of security standards can leave IoT devices open to attack, and this can include hacker attacks as well.
- Vulnerabilities in open-source IoT firmware: Many IoT devices are built with open-source firmware, which can be vulnerable to attacks.
IoT Security Solutions
There is no single solution that can protect all IoT devices from all types of threats. Below is the list of solutions that can help in protecting IoT devices:
- Physical Security: Physical security is essential for avoiding unwanted access to a device because IoT applications are frequently remote. Using durable parts and sophisticated hardware that makes accessing data more challenging is beneficial in this situation.
- Protection against remote access: A strong security mechanism for remote access is required that permits– SIM capability restricted to particular devices.- In the event of a physical security compromise, the capability to remotely terminate connections.
- Private networks: There is a security risk whenever messages are sent and received via remotely deployed devices. These messages are susceptible to interception when devices are connected, and communication is enabled over public-access networks like Wi-Fi.While using public networks to communicate sensitive data calls for additional care, encrypting messages is a good first step. Private networks guarantee that data never travels via the open Internet on top of the current security measures.
- Encryption: Protect data from unwanted access by encrypting it while it’s in transit and at rest. This covers safe data storage on devices and encryption of communication channels.
- Updates to the firmware and patch management: Update firmware frequently and install security patches to fix bugs and guard against exploits. This entails setting up procedures for timely patching and guaranteeing interoperability with IoT devices.
- Blockchain Techniques: The integration of blockchain technology improves the transparency and integrity of IoT data transfers. Distributed ledger technology strengthens trust and accountability by guaranteeing data immutability and offering a tamper-proof record of device interactions.
- Intrusion Detection Systems (IDS): By deploying IDS sensors, network traffic is observed for unusual activity, and administrators are notified of possible security breaches. IDS systems assist in quickly identifying and mitigating security events and offer real-time threat detection.
eInfochips, with its extensive experience in creating, building, and managing secure connected products across devices, faced a challenge to develop secure, market-ready solutions to strengthen IP camera security. This involves covering firmware, data encryption, and physical security. To overcome the challenge, eInfochips integrated threat modeling, secure product design, software analysis, penetration testing, and SD aspects into a comprehensive security requirement management system. Read more about the Industrial IP Camera Security Enhancement Solution case study, here.
Why eInfochips?
eInfochips provides end-to-end security solutions that protect the entire information lifecycle, from collection and storage through transmission and delivery. By protecting data at every stage, these solutions help organizations prevent data breaches and protect their customers’ information. For comprehensive protection, they also offer Security Testing Services to ensure robust security measures are in place.
Some end-to-end security solutions include:
- Development of Secure IoT products: We incorporate various layers of security measures throughout the lifecycle of product development to ensure the security of IoT products. To safeguard products from the root, we have been using a secure by design strategy. We incorporate security by design and Vulnerability Assessment and Penetration Testing (VAPT) testing into your product development lifecycle as part of our security workflow. This approach ultimately helps customers to deploy secure products in the open world that helps protect products from IoT security-related threats.
- Data security solutions: These solutions can help protect data by encrypting and securing it in a manner that prevents unauthorized access.
- Data Loss Prevention (DLP): DLP solutions can help in preventing data loss by identifying and blocking unauthorized access, copying, and transmission.
- Data governance solutions: These solutions can help organizations manage their data securely by ensuring that it is accessed only by authorized personnel, stored in a secure location, and protected from unauthorized changes.
Using a strategic, transformational, and managed operations strategy, eInfochips has assisted enterprises in developing, deploying, and managing security solutions on a worldwide scale by protecting their connected device networks spanning device-connectivity-application levels. We offer cybersecurity expertise in threat modeling and VAPT across devices, operating systems/firmware, web/mobile applications, data, and cloud workloads in accordance with security industry standards, regulations, and guidelines such as OWASP, MITRE, ENISA, NIST, and IoT Security Foundation.
Emerging Trends in IoT Security Threats
IoT has brought about remarkable innovations, connecting devices, and systems in ways that were once unimaginable. However, this interconnectedness also brings forth new and evolving security threats. To stay ahead in the battle of IoT security, it’s crucial to understand the latest trends in IoT security threats.
1. Ransomware Targeting IoT Devices
Trend: Ransomware attacks are increasingly targeting IoT devices, encrypting their firmware, and demanding ransom for decryption keys.
Impact: A successful attack can disrupt critical IoT systems, such as industrial controls or medical devices.
Mitigation: Regularly update firmware, implement strong authentication, and have backup systems in place to minimize damage from ransomware attacks.
2. Ransomware Targeting IoT Devices
Trend: Ransomware attacks are increasingly targeting IoT devices, encrypting their firmware, and demanding ransom for decryption keys.
Impact: A successful attack can disrupt critical IoT systems, such as industrial controls or medical devices.
Mitigation: Regularly update firmware, implement strong authentication, and have backup systems in place to minimize damage from ransomware attacks.
3. AI-Enhanced Attacks
Trend: Attackers are using Artificial Intelligence (AI) and Machine Learning (ML) to find vulnerabilities and devise more sophisticated attack strategies.
Impact: AI-driven attacks can adapt and evolve rapidly, making them harder to detect and mitigate.
Mitigation: Incorporate AI and ML into your security strategy to proactively identify and respond to evolving threats.
4. Supply Chain Attacks
Trend: Targeting the supply chain to compromise IoT devices.
Impact: Compromised devices may have backdoors or malware embedded, posing a significant risk to users.
Mitigation: Establish a robust supply chain security framework, conduct thorough vetting of suppliers, and implement device integrity checks.
5. 5G Vulnerabilities
Trend: The rollout of 5G networks introduces new attack surfaces, as more devices connect at high speeds and low latency.
Impact: Faster connectivity may lead to quicker exploitation of IoT vulnerabilities and more significant data breaches.
Mitigation: Implement security measures specific to 5G networks, such as network slicing and secure authentication.
6. Legislation and Compliance Challenges
Trend: Governments and regulatory bodies are increasingly introducing IoT security requirements and regulations.
Impact: Non-compliance can result in legal consequences.
Mitigation: Stay informed about IoT security regulations in your region and ensure your IoT systems adhere to these standards.
7. Weaponization of IoT Devices
Trend: Cybercriminals are repurposing IoT devices, such as cameras and routers, into botnets for launching attacks.
Impact: Large-scale attacks can overwhelm networks, causing downtime and service disruptions.
Mitigation: Employ network traffic analysis, intrusion detection systems, and access controls to identify and block malicious traffic.
8. IoT Device Ecosystem Vulnerabilities
Trend: IoT devices often rely on a complex ecosystem of components and third-party services, creating potential weak links.
Impact: Vulnerabilities in any part of the ecosystem.
Mitigation: Regularly update all components, perform security assessments, and ensure third-party services adhere to security best practices.
9. Quantum Computing Threats
Trend: Quantum computing threatens to break current encryption algorithms, potentially exposing IoT device data.
Impact: Sensitive data may be at risk if quantum computers become capable of cracking encryption.
Mitigation: Explore quantum-resistant encryption algorithms and be prepared to transition to them when necessary.
10. IoT Security Awareness
Trend: As IoT adoption grows, security awareness among users and organizations becomes increasingly critical.
Impact: A lack of awareness can lead to poor security practices.
Mitigation: Invest in IoT security education and training for both users and IT personnel.
Conclusion
The IoT security landscape is continually evolving. Staying ahead of emerging threats is paramount in such a scenario. Organizations and individuals must remain vigilant, adopt advanced security measures, and adapt to the ever-changing threat landscape to ensure the safety and integrity of their IoT Solution And Services ecosystems. As IoT technology continues to advance, so too must our defenses against evolving security threats.













