With exponential growth in the number of IoT devices in all sectors and the number of cyber-attacks is also increasing thus developing secure IoT devices is the prime requirement. There are no specific rules/standards for secure IoT device and rules/standards are different in different regions so the minimum criteria can be followed which can provide maximum security and compliance with almost all standards. Please refer to the connected device and cyber-attacks trends:
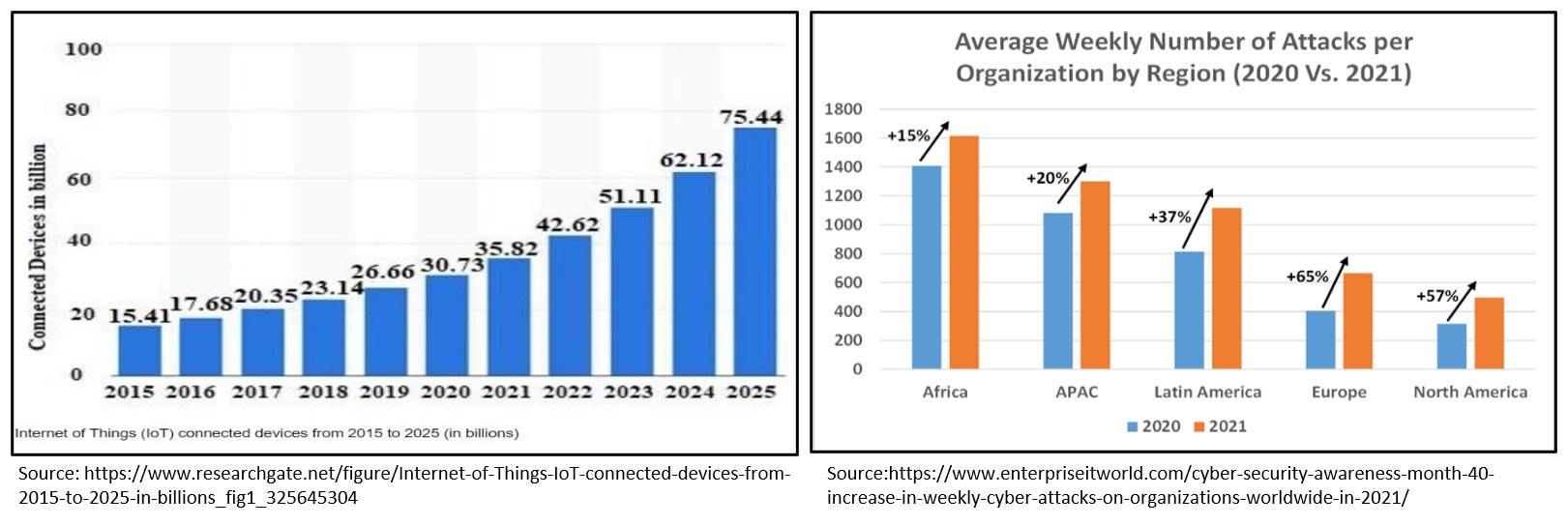
Per the above trends, with the number of connected devices, attacks are increasing in every region of the world. Further, please refer to the trends of vulnerability:
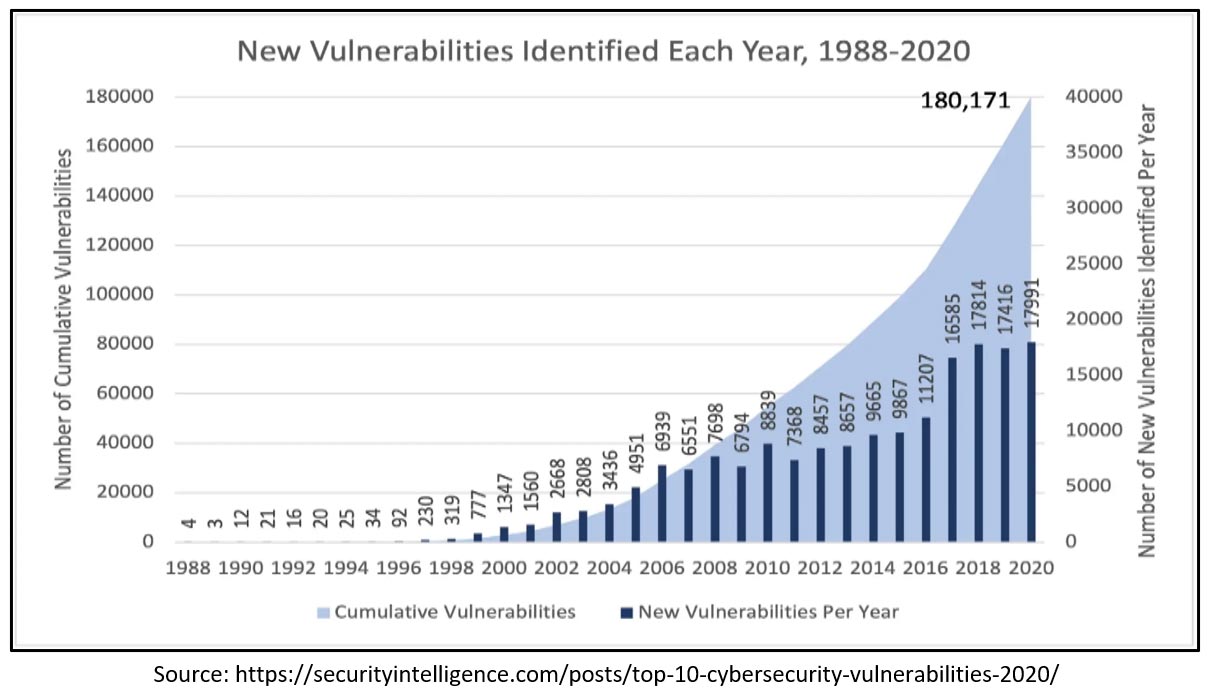
Above vulnerability trend indicates that the chances of attacks on IoT devices is increasing.
That said, to be ahead of threats on IoT devices, we need to develop secure and penetration proof IoT devices by design. Secure devices can be developed by following specific processes and by adding specific validations in the firmware. The secure device development process and validations are explained in the subsequent sections.
The Secure Device Development Process
By following the below processes, secure devices can be developed by design. Let’s explore each sub-process in detail

Threat Modeling
This is a process for identifying potential threats to the system.
During this process, need to find out the answers to the following questions:
- What do we build?
- What can go wrong?
- How can we mitigate that?
Tools are available in market that can be used for the threat modeling:
- Microsoft Threat Modelling Tool (TMT)
- Threat Dragon
- Cairis
- Kenna VM
Threat modeling can help in identifying different types of threats like spoofing, tampering, information discloser, denial of service, elevation of privilege, etc. The following snippet describes a way to model an IoT device in the Microsoft Threat Modeling Tool

Secure Architecture
In this stage, a secure architecture must be designed based on threats identified in the threat modelling stage. During this process, there is a need to find out the answers to the following questions:
- What is the product (PC, Music System, Home Appliance, etc.)?
- What is the use of this product?
- How to design?
This is the most important stage of the product development process as an extreme level of technical competency is required to create hardware and software architecture. While preparing the architecture, need to address the security of the following layers
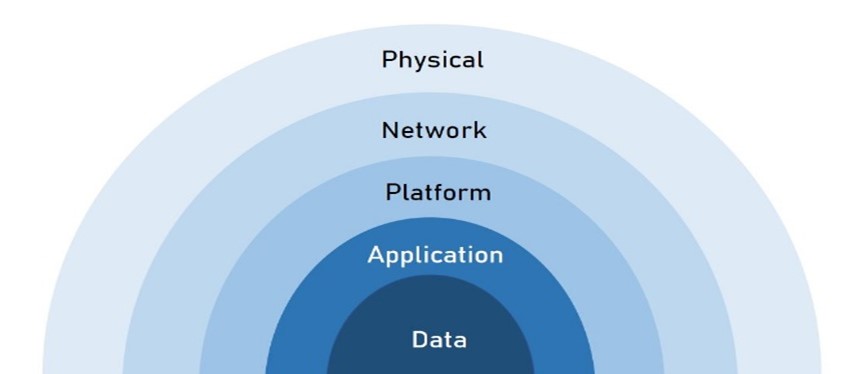
Tamper proof and robust device hardware need to be designed to mitigate physical security. Protocols and interfaces used for external world communication need to be reviewed and secure most need to be selected to mitigate the network security. To mitigate the platform security, Operating systems and the controlling devices based on how secure they are. User applications need to be developed by following secure coding standards and resolving issues reported by static code analyzer tools. The most important entity is “Data” so it must be protected, and it must not be allowed to access without authentication and authorization.
Secure Development Life Cycle (SDLC)
In this process, the secure system will be developed. In 2002, Microsoft had developed a method to mitigate damage from the cyber-attacks, and now, it is known as SDLC. This is a group of activities that can help to develop secure products. Please refer to Microsoft’s security development lifecycle practices for detailed information.
Testing
This is a process of validating that the developed device is secure. There are different ways of testing as follows:
● Black Box Testing
In this method, the minimum information is provided to the testers, and they have to collect product information like protocols, libraries, kernel, and respective versions used after that try to find any vulnerability of the product. This is time consuming process. This process maps with the real-world scenario in which hackers hack IoT devices with minimal product information.
● White Box Testing
In this method, detailed product information is provided to testers, and based on that they find out the vulnerabilities. This test method helps to confirm that the product cannot be hacked with known product architecture and detailed information.
● Grey Box Testing
In this method, partial information is provided to the testers, and based on that they search and identify the defects. Using this method, the overheads of long functional/non-functional testing can be reduced. This test method will help to get the combined benefit of the white and black box testing. All the layers of any complex system can be covered using this test method.
Based on the type of product and end-users, any of the above methods can be selected.
Production
This is a process to make sure that the system is still secure during production.
The following sub-activities need to perform during this process:
- Security Review
- Penetration Testing
- Plan to Mitigate New Vulnerabilities
- Deploy Updates/Fixes
Common Attacks, Vulnerabilities and Mitigations
In this section, the different types of attacks and vulnerabilities with their mitigations will be explored.
SQL Injection
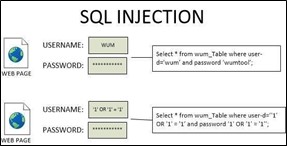
This is one of the most common attacks. It exploits the SQL database by inserting the malicious code into SQL queries. Please refer to the following image for more information:
In this image, SQL query is provided in username and that will cause failure in the device authentication process and either access of the device or return user-id table. Please refer SQL injection attack demo for more detail.
To protect the device from this attack, the special characters must be prevented in user input fields. Further, server must validate the input string in the frontend and backend before processing the user inputs.
Cross-Site Scripting

This attack is performed by injecting malicious JavaScript into the user fields. The injected script can access the sensitive information of the device like cookies, user details, session tokens etc. These scripts can even update the content of the webpage. Please refer to the image for more information. Please refer to cross site scripting demo for more understanding:
To protect the device from this attack, allow only required special characters in user input fields. For example, the user input field for email address must allow uppercase and lowercase letters, digits, and limited special characters (! # $ % & ‘ * + – / = ? ^ _ ` { |). Further, the length of the user input fields must be limited. For example, no need to allow 64 characters in the email address field. The data from user input field can be copied to application buffer by providing the maximum allowed length.
Denial of Service
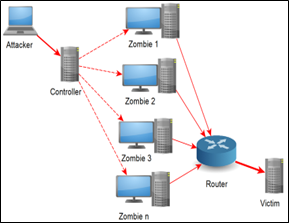
This attack is generally accomplished by sending the superfluous queries to the targeted IoT devices either from one machine or globally distributed machines to stop some or entire services of the device.
There are three main types of this attack:
- Application-layer attacks
- Protocol attacks
- Volumetric attacks
Please refer to the image for more information.
Please refer to BrakTooth – Feature Response Flooding on Audio Products for more understanding:
To protect the device from this attack, redundant communication ports should be disabled. The device discovery should also be disabled. Continuous monitoring of the network traffic, and sensing typical network activity, and traffic patterns should be incorporated into the product.
Unencrypted Communication
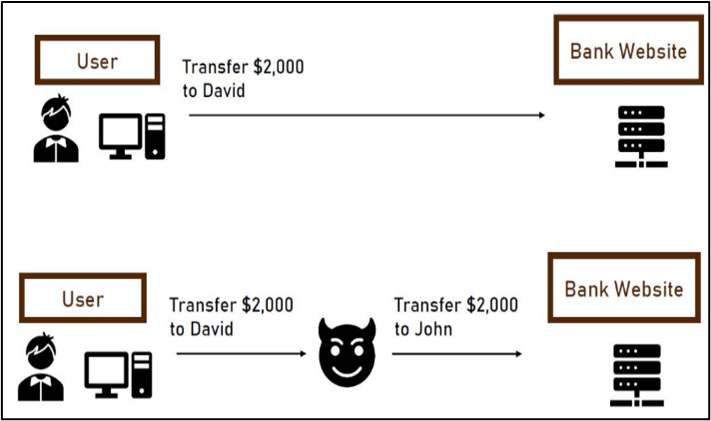
This is the vulnerability of the product which hackers can use for malicious activities. If the data is transmitted in the clear text format over the communication channels, then Man in Middle can sniff and change data. Please refer to the following image for more information.
Please refer to MITM video for more detail
The transport layer security (SSL/TLS) can be used to prevent this threat. For now, TLS v1.3 is the latest and recommended.
Weak Hashing Method
The sensitive data is encrypted using the weak hashing method or not using data encryption is similar as the weak hashed data can be decrypted in a few seconds by the hacker. Md5sum, SHA-0, SHA-1, base64, etc. are considered weak hashing methods. SHA256, SHA512, BLAKE2, RIPEMD-160, etc. are considered strong hashing methods.
For strong data encryption, Advanced Encryption Standard (AES) with salt can be used.
Unauthorized Access
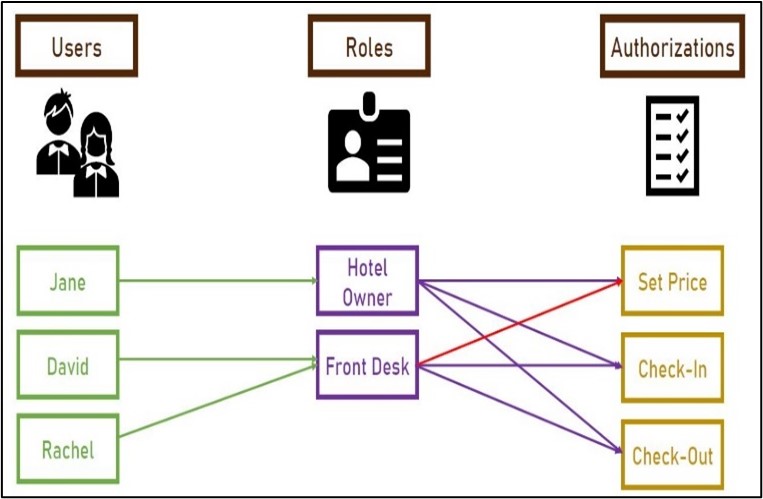
This is a vulnerability of the product which provides access to restricted data to unauthorized users. The unauthorized user can expose the restricted data or update the existing data for own benefit. Please refer to the following hotel example for more understanding:
The role-based access system can be incorporated into the server so that only authorized users can access the data. As shown in the image, Front Desk employees should not allow setting prices, but the hotel owner should have all the permissions. Initially, minimal permissions should be provided to all the users and privileged access should be provided on demand. Further, privileged access should be removed immediately after the completion of the task. Alerts can be incorporated into the system to warn the owner when unauthorized access is attempted.
Data Exposer
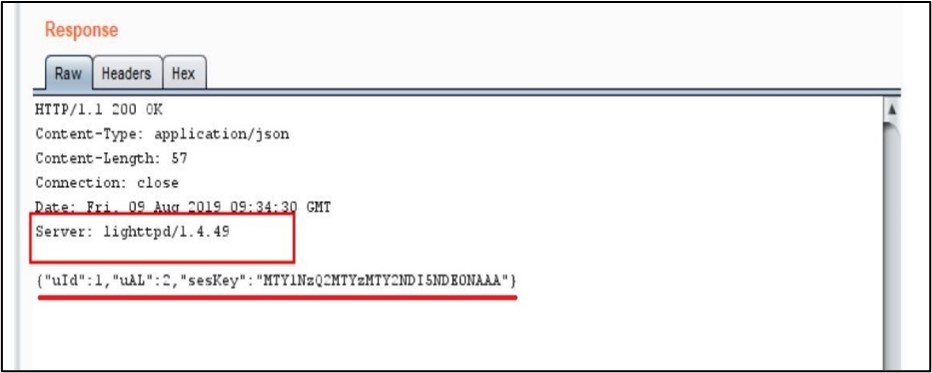
This is a flaw of the device in which the device discloses sensitive information to the external world and this information can be used for hacking the device. In the shared image, the server is disclosing its version number. If a hacker gets this information, then he can apply hacks related to this version and this will help him to reduce hacking time.
Further, IoT devices are dumping the information on the console, and that can be easily captured by unauthorized persons.
External ports like console and JTAG must be disabled before installing a device in the field. Further, firmware must be updated to stop disclosing sensitive information in clear text format.
There are many other points to be taken care of like Default credentials, Use of insecure Third-party tools, Source Code Accessibility, Secure Boot, Secure OTA, Encrypting Memory Partitions, Thread-safe User Applications, Memory Protection, etc.
Cyber Security Assessment of the IoT Device
The Open Web Application Security Project (OWASP) is a foundation that works to improve the security of software. Multiple projects are driven by the OWASP foundation like OWASP Amass, Application Security Verification Standard, API Security Project, OWASP Top 10, OWASP Penetration Testing Kit, etc. Please refer to the OWASP link (https://owasp.org/) for more information. Some labs like TuV are providing the facility of cyber security assessment of the IoT devices. Please refer to the TuV Link (https://www.tuvsud.com/en-in/services/testing) for more information.
Conclusion
eInfochips has strong competency in the design and development of secure customer products. Our expertise in IoT Solution And Services, Cybersecurity consulting services, and Hardware Design on different platforms has helped us to create meaningful value for customers across industry verticals including Industrial Metering Devices, Electric vehicle chargers, Wearable devices, Medical Equipment, etc.