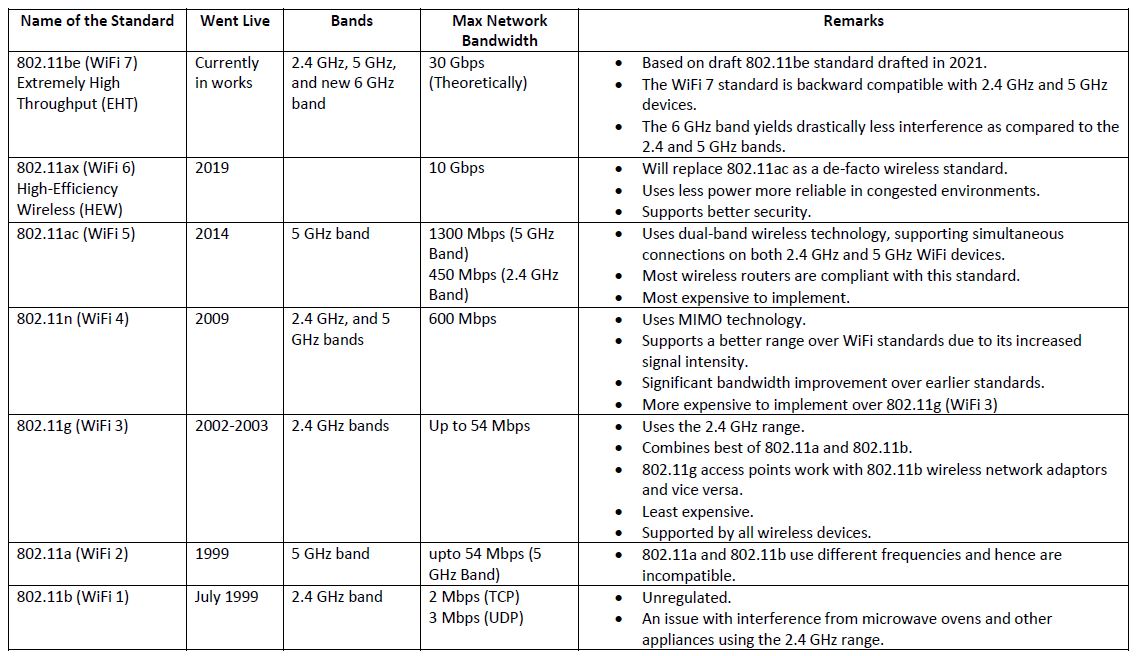
WiFi Standards
The first WiFi standard was defined in 1997 and is obsolete. There will hardly be any devices compatible with that standard now. The first WiFi standard was followed by WiFi 1 to WiFi 6 standards, briefly described in the table below. WiFi 7 is under development and will be available to the public by 2024. Many other WiFi standards stand in between the ones mentioned in the table below, namely, IEEE 802.11ad, IEEE 802.11af, IEEE 802.11ah, IEEE 802.11ai, IEEE 802.11aj, IEEE 802.11aq, IEEE 802.11ay, and IEEE 802.11ba.
Carrier Sense Multiple Access (CSMA) with Collision Avoidance
CSMA is a method that allows more than two devices connected over the same transmission line to share their capacity. The CSMA works on the data-link layer (Layer 2) of the OSI model. The collision avoidance module attempts to avoid collision on the transmission medium by sensing if the channel is idle, and only then transmitting the data frame across. If the channel is not idle, collision avoidance is achieved by waiting for a certain period before it checks for the idleness of the channel.
2.4 GHz and 5 GHz Bands
For the standards defined till now, two bands have been used in most of the standards mentioned above ─ the 2.4 GHz and 5 GHz bands.
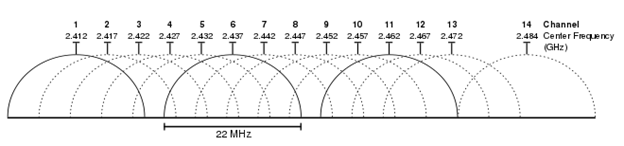
The 2.4 GHz band is used by 802.11b, 802.11g, and 802.11n standards, and the band ranges from 2.4 GHz to 2.4835 GHz. The 2.4 GHz band is divided into 14 frequency channels, where each channel is 20 MHz wide as shown in the picture below. In the USA, channel numbers 12 and 13 are invalid. Channel 14 is unusable as it goes beyond range. There’s a 5 MHz gap between adjacent channels and hence we can observe the overlaps in the channels. Therefore, only three non-interfering channels are kept active at any given time. They are Channel numbers 1, 6, and 11. One cannot use Channels 2, 7, and 12, OR Channels 3, 8, and 13; as 12 and 13 are banned for use by the USA. The 2.4 GHz range is pretty crowded as many other devices as possible like microwaves, cordless phones, and Bluetooth devices are active on the same band, thus making it susceptible to interference.
The 5 GHz band is used by 802.11a, 802.11n, and 802.11ac standards, and it consists of 24 bands, each 20 MHz wide. As there is no overlapping among the 24 channels in the 5 GHz band, it is much less congested when compared to the 2.4 GHz band. To increase the bandwidth, ‘Channel Bonding’ is used, wherein two 20 MHz channels are combined to yield a 40 MHz wide channel. In the 802.11ac standard, two 40 MHz channels are combined to form an 80 MHz wide channel. Even two 80 MHz channels are combined to get a 160 MHz channel. Hence, it is possible to achieve higher data rates and higher data accuracy for the 5 GHz band.
Range and Bandwidth of WiFi
The range decides the distance for which data can travel. It has been observed that the higher the frequency of a wireless signal, the shorter its range because the higher frequency signals cannot penetrate solid objects when compared to the low-frequency signals. Thus, data on the 5 GHz band travels a shorter distance when compared to the 2.4 GHz band.
Higher bandwidth enables faster upload and download speeds. Hence, applications that consume high bandwidth such as streaming video services appear smoother and faster on 5 GHz as compared to 2.4 GHz. The decision to use a particular band (2.4 GHz or 5 GHz) depends on the type of data and the range at which it is to be transferred.
Signal Modulation of Wireless Signals
Interference and jamming slow down transmission in wireless signals. Besides that, the interception of data in a band of WiFi signals can become a huge security problem. Various signal modulation techniques are thus used to prevent the same. FHSS (Freq. Hopping Spread Spectrum) and DSSS (Direct Freq Spread Spectrum) are the two most used signal modulation methods.
FHSS uses the spread spectrum technique, wherein a signal generated with a particular bandwidth is deliberately spread within each frequency band to help reduce interception, detection, jamming, and interference. The frequency hopping pattern is only known to the receiver and sender. Different senders and receivers use unique hopping patterns, and those patterns change over a period making it difficult to interpret the data even if a hacker tried to intercept and capture the data.
DSSS combines data signals directly with a higher bit-rate sequence. For this, a Pseudo Noise sequence is added to the data. The Pseudo Noise sequence is a higher bit rate sequence of zeros and ones. These sequences are used to make the original data signal identical to the Pseudo Noise sequence. At the receiving end, these modulated signals are demodulated with the Pseudo Noise sequence to get the original data signal back.
WiFi Data Framing
The WiFi data frames are grouped into management frames, control frames, and data frames as described below:
Management Frames: The management frames contain bit or byte sequences for the wireless association, re-association, probe, and beacon. They also contain bits, specifying stations joining and/or leaving WiFi networks. A beacon frame is a continuous announcement of an access point’s existence. The ‘beacon’ lets us know about the networks nearby that are accessible by our device. When the WiFi settings on a device are opened, one can observe the different ‘access points’ that are available.
Probe frames are opposite of beacon frames. The devices usually keep probing which networks are accessible. The device remembers the details about the network. If the network that the device had earlier connected to, is available, the authentication and association processes start to connect to that network.
Control Frames: The control frames contain bit or byte sequences for WiFi medium access, and data delivery; e.g., RTS (Request to Send)/CTS (Clear to Send) frames in CSMA/CA (described above), and ACK (acknowledge), Block-ACK (block acknowledge) frames. The control frames “control” the medium and aid in the delivery of other frames.
Data Frames: They contain the data to be sent from the sender to the receiver. Data frames carry higher-level protocol data. They may contain three types of data i.e., actual data, QoS (Quality of Service) data, and NULL data.

Frame Control (2 bytes) — Contains information of the protocol being used, and the type of frame (the type of security that is used).
Duration (2 bytes) — Time duration of the frame so that other channels know when will the frame end.
Address 1 (6 bytes) – The sender’s MAC address.
Address 2 (6 bytes) — Transmitter’s address that refers to transmitter access point’s MAC address.
Address 3 (6 bytes) — Receiver’s address that refers to receiver’s access point’s MAC address.
Sequence Control (2 bytes) – Indicates how a large packet is fragmented.
Address 4 (6 bytes) — Destination/recipient MAC address.
QoS Control (0 to 2 bytes) – QoS control field (indicating access category, policy type, and payload type).
HT Control (0 to 4 bytes) – High throughput control frame.
Frame Body (0 – 2312 bytes) – Data to be sent across (payload).
Frame Check Sequence (6 bytes) – CRC check.
Conclusion
WiFi /wireless communications technology has surpassed the ethernet (RJ45) connectivity technology because of the mobility factor that it provides. At the same time, the use of electromagnetic waves has introduced new technical challenges. Most of the radio bands are being utilized by various governments and hence the restrictions in the bandwidth usage have resulted in overcrowding of bands as well as security challenges. The IEEE is working on new algorithms and technologies to use these bands more securely and efficiently.
The data transmission rate through the WiFi medium is much lower than the wired medium, but the WiFi 7 technology is trying to overcome that challenge as well, by achieving speeds of nearly 30 Gbps.
eInfochips – An Arrow Company provides end-to-end services and solutions in designing, optimizing, and implementing WiFi hardware and firmware (application) solutions. We also provide design services and support for troubleshooting wireless network issues.
For further information about the services that we offer, contact our experts today.
References
https://en.wikipedia.org/wiki/IEEE_802.11












