The rising threat of cybercrime is a major concern for both individuals and businesses, as it can cause significant financial losses and damage reputations. According to predictions by Cybersecurity Ventures, the annual cost of cybercrime is expected to reach USD 8 trillion by 2023, with the cost of damages projected to increase to USD 10.5 trillion by 2025.
Among the numerous cybersecurity threats, Trojan malware is one of the most stealthy and dangerous. This malicious software can enter computer systems undetected and allow attackers to gain unauthorized access to sensitive data. Cybercriminals are continually developing more sophisticated tactics and exploiting vulnerabilities in software and hardware, making it increasingly challenging to prevent these types of attacks.
According to AV-Test, in 2019, trojans were identified as the top choice for cybercriminals to breach Windows systems. Trojans made up 64.31% of all malware attacks on Windows systems during the measured period, while viruses accounted for 15.52% of attacks.
Trojan malware is a form of malware that often infects a user’s device after being downloaded for free or as an attachment to an email. Malicious code can be used to steal money, track internet users’ actions, or gain access to enterprise systems and confidential information.
What is a Trojan?
A Trojan, also known as a Trojan horse, is a type of malicious software that appears to be legitimate software but contains hidden malicious code. Trojans can take many forms, including emails, attachments, files, or software programs. They can be designed to do a variety of malicious activities, such as stealing sensitive information like passwords or credit card numbers, spying on user activities, or providing unauthorized access to an attacker. Trojans typically rely on social engineering tactics to convince users to download and execute them, often by disguising themselves as legitimate files or software.
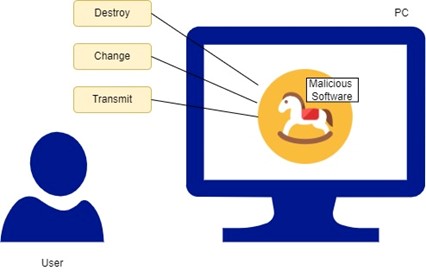
Once a Trojan is installed on a computer, it can allow the attacker to gain remote control of the system, enabling them to carry out malicious activities without the user’s knowledge or consent. To protect your computer from Trojans, it’s important to use antivirus software, keep your operating system and software up to date with the latest security patches, be cautious when opening email attachments or downloading files from the internet, and avoid visiting suspicious or untrusted websites. It’s also important to understand how intruders work and what steps you can take to protect your devices.
How do Trojans Work?
One of the most common online hazards, Trojans, can harm both individuals and businesses. While in the past, most attacks targeted Windows or PC users, the rise in Mac users has increased macOS threats, putting Apple aficionados at risk of this security concern. Trojans can also attack and infect tablets and smartphones using a branch of mobile malware. This can happen when an attacker reroutes traffic to a Wi-Fi network-connected device, which they then use to perform cyberattacks. Additionally, Trojans can infect mobile devices such as phones and tablets.
Users may inadvertently infect their devices with Trojan malware through common actions such as:
- Downloading illegal content, such as music, software, movies, books, or video games.
- Downloading any unsolicited files or attachments, even from well-known sources.
- Accepting pop-up notifications without understanding or reading their messages.
- Ignoring user agreements when downloading legal applications or software.
- Neglecting to install updates and patches for software, the operating system, applications, and browsers.
Common Types of Trojan Malware
Here are descriptions of some of the most common types of Trojan viruses:
Trojan Backdoor
This virus can give attackers access to a computer and control it, allowing them to download and steal data or download other malicious software to the device.
Trojan Horse for DDoS Attacks
This malware carries out distributed denial-of-service (DDoS) attacks, overloading a network with traffic to bring it down. Both the infected computer and other computers can generate that traffic.
Trojan Downloader
This Trojan targets computers that are already infected, and installs new versions of harmful software, such as adware and malware.
Fake AV Trojan
This Trojan behaves like antivirus software but asks for payment before it can identify and eliminate any real or imagined threats.
Game Thief Trojan
This Trojan targets online gamers and steals their account information.
Data-Stealing Trojan
This Trojan steals data from compromised PCs.
Trojan-Mailfinder
This Trojan’s goal is to collect email addresses from the infected device.
Trojan Ransomware
This Virus demands a ransom to repair the damage it has caused to the machine, such as blocking access to data or reducing computer performance.
Rogue Access Tool
This Trojan can gain remote control of a computer, steal information, or spy on the user.
Rootkit Virus
This virus is intended to hide or obscure an object on an infected computer, to prolong the period a harmful program is active on the device.
Trojan-SMS
This type of Trojan infects mobile devices and can send and intercept text messages, potentially leading to increased phone expenses if messages are sent to premium-rate lines.
Malicious Banker
This Trojan aims to access bank accounts and steal login information, including banking, credit card, and bill-paying information.
IM Trojan
This Virus targets instant messaging sites and steals login information and passwords.
Examples of Trojan Malware Attacks
Attacks using Trojan viruses can have a significant impact, and Trojans are constantly evolving. Here are two examples:
Rakhni Trojan
This malware has been in existence since 2013 and has recently been able to infect computers with ransomware or a cryptojacker, which enables thieves to mine cryptocurrency using your device. According to the 2018 Internet Security Threat Report, coin mining experienced tremendous growth in the latter months of 2017.
ZeuS/Zbot
Another dangerous malware, this banking Trojan may be dated but it still poses a threat. ZeuS/Zbot’s code was initially made available in 2011. It records your keystrokes as you log into your bank account, using keystroke logging to steal your login information and possibly your account balance as well.
Methods for Preventing Trojans
Here are some tips to avoid Trojan malware: dos and don’ts. First, the dos:
- Securing a computer starts with setting up and using an internet security suite. It is also important to conduct regular diagnostic scans using the security application. You can set up the software to automatically run scans at scheduled intervals.
- Updates for your operating system and other computer programs should be installed as soon as they become available. Outdated software can be exploited by cybercriminals, compromising your computer’s security.
- To protect your accounts, use unique passwords that are a mix of letters, numbers, and symbols. Use firewalls to keep your personal information secure.
- Regularly backing up your files will help you recover your data if your computer gets infected with a Trojan.
- Finally, use caution when opening email attachments. Always inspect attachments to keep your computer safe.
Ensuring the security of IoT/OT technology equipment is crucial for every business. A company must have security measures in place for its IoT devices to protect its assets, data, and infrastructure from potential threats. By implementing security measures, a business can reduce the risk of a successful attack and minimize the impact of an event, if it occurs. We have 360-degree cybersecurity expertise in threat modeling and VAPT (Vulnerability Assessment and Penetration Testing), covering devices, OS/firmware, web/mobile apps, data, and industry security standards and guidelines, such as NIST, ENISA, OWASP, MITRE, and IoT Security Foundation.
eInfoprivacy%20standards%2C%20regulations%20across,using%20diverse%20cybersecurity%20platform%20services%chips has helped businesses manage security products on a global scale by protecting connected device networks across the device-connectivity-application layers using strategic, transformative, and managed operational techniques. We provide comprehensive cybersecurity expertise for threat modeling and VAPT across OT/IoT devices, OS/firmware, web/mobile apps, data, and cloud workloads to meet security industry standards, rules, and guidelines. Contact us to learn more about our cybersecurity solutions.