As part of eInfochips Cybersecurity consulting services, we have developed a score-based Assessment Framework across three phases. Each phase comprises of set of questions to assess the overall Cybersecurity maturity of the product/application in scope.
The first phase of the framework focuses on gathering critical product and application details as a foundation for security planning. During this phase, which spans one week, the Security Architect is responsible for identifying and understanding the product’s components, including hardware, firmware, and communication protocols. The phase also involves evaluating software platforms such as cloud, web, mobile applications, and APIs, as well as analyzing data handling practices. Ensuring compliance with industry standards and regulations is a key focus, alongside identifying the product’s target market.
In the second phase, the Security Architect conducts a High-level assessment covering key security areas including Device Design & Architecture, Authentication & Authorization mechanisms, Firmware & Software Security, Communication, Network, and Physical Security, Third-Party Integrations & Supply Chain Security and Vulnerability Management.
In the final phase, the Security Architect conducts four key assessments. The Operational Assessment covers personnel, physical security, governance, and business continuity, involving HR, IT, admin, and security teams. The Product Lifecycle Assessment evaluates risk management, design, security testing, and deployment. The Product Security Assessment focuses on authentication, encoding, access control, and encryption. Lastly, the Operational Supplier Audit includes network and physical audits along with security testing to assess third-party risks.
In the end, we present a detailed Gap Analysis Report covering Assessment process, findings and recommendations.
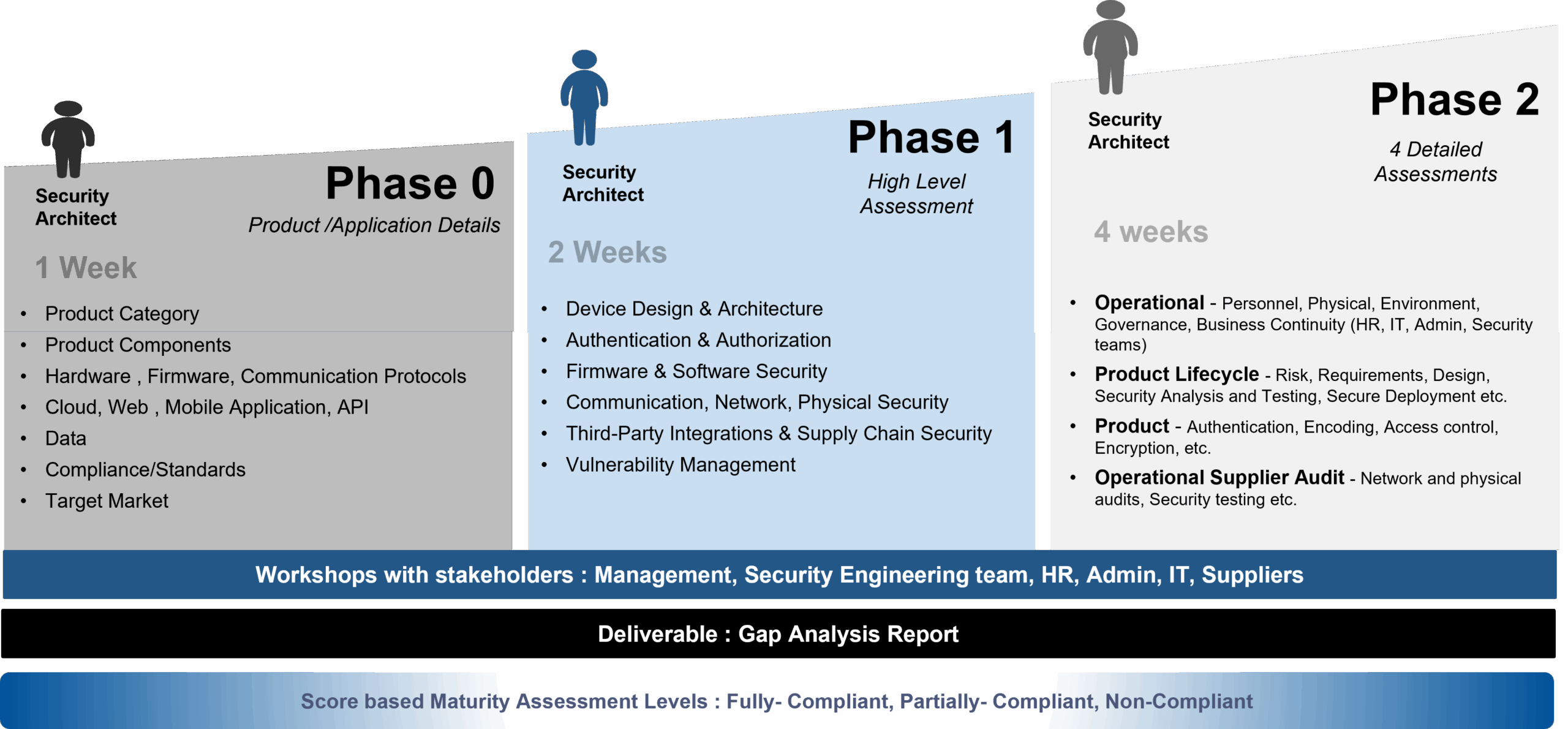
The assessment framework describes three levels of maturity:
Schedule a 30-minute consultation with our Automotive Solution Experts
Schedule a 30-minute consultation with our Battery Management Solutions Expert
Schedule a 30-minute consultation with our Industrial & Energy Solutions Experts
Schedule a 30-minute consultation with our experts


